Overview
This chapter provides an overview of Virtual eXtensible Local Area Network (VXLAN) and its implementation with OcNOS. VXLAN creates LAN segments using a MAC in IP encapsulation. The encapsulation carries the original L2 frame received from a host to the destination in another server using IP tunnels. The endpoints of the virtualized tunnel formed using VXLAN are called VTEPs (VXLAN Tunnel EndPoints). This technology allows the network to support several tenants with minimum changes in the network. The VTEPs carry tenant data in L3 tunnels over the network. The tenant data is not used in routing or switching. This aids in tenant machine movement and allows the tenants to have the same IP or MAC addresses on end devices, hosts/VM’s.
OcNOS supports VxLAN IPv4 tunnels, but both IPv4 and IPv6 hosts are supported.
Terminology
Terms related to VXLAN configuration are defined in the table below.
IGMP | Internet Group Management Protocol |
PIM | Protocol Independent Multicast |
VLAN | Virtual Local Area Network |
VM | Virtual Machine |
VNI | VXLAN Network Identifier (or VXLAN Segment ID) |
VTEP | VXLAN Tunnel End Point. An entity that originates and/or terminates VXLAN tunnels |
VXLAN | Virtual eXtensible Local Area Network |
VXLAN Segment | VXLAN Layer 2 overlay network over which VMs communicate |
VXLAN Gateway | An entity that forwards traffic between VXLANs |
VXLAN Architecture
VXLAN runs over the existing networking infrastructure. It provides a means to “stretch” a Layer 2 network. In short, VXLAN is a Layer 2 overlay scheme on a Layer 3 network.
Each overlay is termed as a VXLAN segment. Only VMs within the same VXLAN segment can communicate with each other. Each VXLAN segment is identified through a 24-bit segment ID termed the “VXLAN Network Identifier (VNI)”. This allows up to 16 million VXLAN segments to coexist within the same administrative domain.
VNI identifies the scope of the inner MAC frame originated by the individual VM. Hence, we can have overlapping MAC addresses across segments but never have traffic “cross over” since the traffic is isolated using the VNI. The VNI is in an outer header that encapsulates the inner MAC frame originated by the VM.
Any packets (including ARP-ND) that are uplifted to the VxLAN CPU queue from any port are rate limited to 500 packets/second. This is done to protect the system and CPU during an ARP storm.
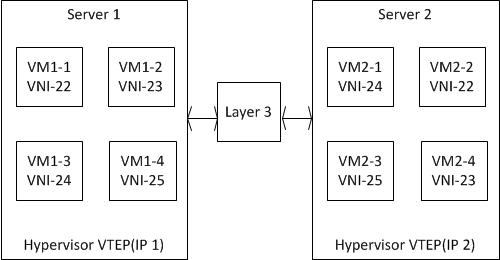
VXLAN Deployment - VTEPs across a Layer 3 Network