802.1X Configuration
IEEE 802.1x restricts unauthenticated devices from connecting to a switch. Only after authentication is successful, traffic is allowed through the switch.
Topology
In this example, a radius server keeps the client information, validating the identity of the client and updating the switch about the authentication status of the client. The switch is the physical access between the two clients and the server. It requests information from the client, relays information to the server and then back to the client. To configure 802.1x authentication, enable authentication on ports eth1 and eth2 and specify the radius server IP address and port.
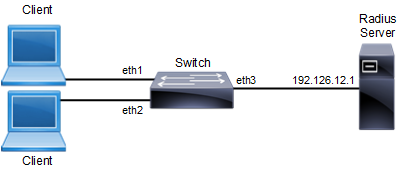
802.1x Topology
Configuration
Switch
Switch#configure terminal | Enter configure mode. |
Switch(config)#port-security disable | Disable the port-security. |
Switch(config)#dot1x system-auth-ctrl | Enable authentication globally. |
Switch(config)#interface eth2 | Enter interface mode. |
Switch(config-if)#switchport | Enable switch port on interface. |
Switch(config-if)#dot1x port-control auto | Enable authentication (via Radius) on port (eth2). |
Switch(config-if)#exit | Exit interface mode. |
Switch(config)#interface eth1 | Enter interface mode. |
Switch(config-if)#switchport | Enable switch port on interface. |
Switch(config-if)#dot1x port-control auto | Enable authentication (via Radius) on port (eth1). |
Switch(config-if)#exit | Exit interface mode. |
Switch(config)# radius-server dot1x keystring testing123 | Specify the key with string name between radius server and client |
Switch(config)#radius-server dot1x host 192.126.12.1 | Specify the radius server address. |
Switch(config-if)#commit | Commit the transaction. |
Switch(config-if)#exit | Exit interface mode. |
Switch(config)#interface eth3 | Enter interface mode. |
Switch(config-if)#ip address 192.126.12.2/24 | Set the IP address on interface eth3. |
Switch(config-if)#commit | Commit the transaction. |
Switch(config-if)#exit | Exit interface mode. |
Validation
#show dot1x all
802.1X Port-Based Authentication Enabled RADIUS server address: 192.168.1.1:60000 Next radius message id: 147
© 2021 IP Infusion Inc. Proprietary 1087
802.1X Configuration
RADIUS client address: not configured 802.1X info for interface eth1
portEnabled: true - portControl: Auto portStatus: Unauthorized - currentId: 29 protocol version: 2
reAuthenticate: disabled reAuthPeriod: 3600
abort:F fail:F start:F timeout:F success:F PAE: state: Connecting - portMode: Auto PAE: reAuthCount: 1 - rxRespId: 0
PAE: quietPeriod: 60 - reauthMax: 2 - txPeriod: 30 BE: state: Idle - reqCount: 0 - idFromServer: 0 BE: suppTimeout: 30 - serverTimeout: 30
CD: adminControlledDirections: in - operControlledDirections: in CD: bridgeDetected: false
KR: rxKey: false
KT: keyAvailable: false - keyTxEnabled: false
802.1X info for interface eth2 portEnabled: true - portControl: Auto portStatus: Unauthorized - currentId: 29 protocol version: 2
reAuthenticate: disabled reAuthPeriod: 3600
abort:F fail:F start:F timeout:F success:F PAE: state: Connecting - portMode: Auto PAE: reAuthCount: 1 - rxRespId: 0
PAE: quietPeriod: 60 - reauthMax: 2 - txPeriod: 30 BE: state: Idle - reqCount: 0 - idFromServer: 0 BE: suppTimeout: 30 - serverTimeout: 30
CD: adminControlledDirections: in - operControlledDirections: in CD: bridgeDetected: false
KR: rxKey: false
KT: keyAvailable: false - keyTxEnabled: false
#show dot1x
802.1X Port-Based Authentication Enabled RADIUS server address: 192.168.1.1:60000 Next radius message id: 147
RADIUS client address: not configured