DHCP Snooping IP Source Guard
Overview
IPSG is a security feature that restricts IP traffic on non-routed, Layer 2 interfaces by filtering traffic based on the DHCP snooping binding database. Use IP source guard to prevent traffic attacks if a host tries to use the IP address of its neighbor. Enable IP source guard when DHCP snooping is enabled on an untrusted interface. After IPSG is enabled on an interface, the switch blocks all IP traffic received on the interface except for DHCP packets allowed by DHCP snooping. A port access control list (ACL) is applied to the interface. The port ACL allows only IP traffic with a source IP address in the IP DHCP snooping binding table and denies all other traffic.
Topology
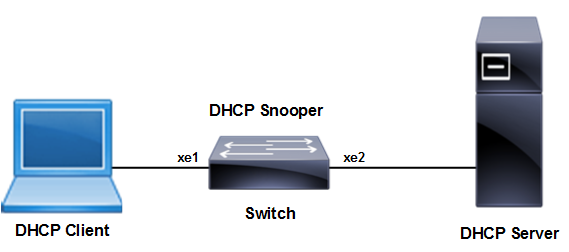
IP Source Guard Topology
Configuring the Ports Connected to DHCP Server and DHCP Client
#configure terminal | Enter the configure mode |
(config)#bridge 1 protocol ieee vlan-bridge | Create IEEE VLAN bridge 1. |
(config)#vlan 2 bridge 1 state enable | Create VLAN 2. |
(config)# ip dhcp snooping bridge 1 | Configure DHCP snooping for bridge 1 |
(config)# ip dhcp snooping information option bridge 1 | Configure DHCP snooping information option 82 |
(config)#cpu-queue vrrp-rip-dhcp rate 0 | Configure DHCP snooping ratelimit. Default value is 100 |
(config)# ip dhcp snooping vlan 2 bridge 1 | Configure DHCP snooping for vlan 2 for bridge 1 |
(config)# ip dhcp snooping verify mac-address bridge 1 | Configure DHCP snooping verify mac-address |
(config)#interface xe2 | Enter Interface Mode |
(config-if)#switchport | Configure the interface as Layer 2 |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode access | Set the Layer2 interface as Access. (It can be Trunk mode also) |
(config-if)#switchport access vlan 2 | Set the default VLAN for the interface |
(config-if)#ip dhcp snooping trust | Configuring the interface as Trust. Basically this is configured on the interface which is connected to Server Side. |
(config-if)#exit | Exit interface mode. |
(config)#interface xe1 | Enter Interface Mode |
(config-if)#switchport | Configure the interface as Layer 2 |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode access | Set the Layer2 interface as Access. (It can be Trunk mode also) |
(config-if)#switchport access vlan 2 | Set the default VLAN for the interface |
(config-if)#ip verify source dhcp-snooping-vlan | Configuring IP source guard at Interface level and configured on the interface which is connected to client side |
(config-if)#ip verify source access-group mode merge | Merge IPSG policy with other ACL |
(config-if)#exit | Exit interface mode |
(config)#ip dhcp snooping binding bridge 1 0011.1111.2222 2 ipv4 1.1.1.1 xe1 | Configure Ipv4 Static Entry For DHCP snooping with MAC address and Source Address for an interface and vlan configured |
(config)#ip dhcp snooping binding bridge 1 0022.2222.3333 2 ipv6 3ffe::1 xe1 | Configure Ipv6 Static Entry For DHCP snooping with MAC address and Source Address for an interface and vlan configured |
(config)#exit | Exit config mode |
#clear ip dhcp snooping binding bridge 1 | Clear DHCP binding tables which are learned dynamically |
Validation
Verify that DHCP snooping is enabled on the bridge:
#sh ip dhcp snooping bridge 1
Bridge Group : 1
DHCP snooping is : Enabled
DHCP snooping option82 is : Enabled
Verification of hwaddr field is : Enabled
DHCP snooping is configured on following VLANs : 2
DHCP snooping is operational on following VLANs : 2
DHCP snooping trust is configured on the following Interfaces
Interface Trusted
--------------- -------
xe2 Yes
DHCP snooping IP Source Guard is configured on the following Interfaces
Interface Source Guard
--------------- ------------
xe1 Yes
Configuring Trusted and Un-trusted Ports
Usually the port connected to server is configured as trusted port and the ports connected to client is configured as untrusted port
In this example, xe1 is connected to the DHCP client and xe2 is connected to the DHCP server.
• Configure xe1 connected to DHCP client as un-trusted port.
• Configure xe2 connected to the DHCP server as trusted port.
#configure terminal | Enter configure mode. |
(config)#interface xe1 | Specify the interface to be configured |
(config-if)#no ip dhcp snooping trust | Disable the port as trusted. |
(config-if)#exit | Exit interface mode |
(config)#interface xe2 | Specify the interface to be configured |
(config-if)#ip dhcp snooping trust | Enable the port as trusted. |
(config-if)#exit | Exit interface mode |
Validation
Verify that static DHCP snooping entries are configured for the bridge:
#sh ip dhcp snooping binding bridge 1
Total number of static IPV4 entries : 1
Total number of dynamic IPV4 entries : 0
Total number of static IPV6 entries : 1
Total number of dynamic IPV6 entries : 0
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- ---------------
0011.1111.2222 1.1.1.1 0 static 2 xe1
0022.2222.3333 3ffe::1 0 static 2 xe1
Configuring IP Source Guard on LAG Port
In this example, the LAG port (sa2) is created, then physical interfaces are added.
#configure terminal | Enter the configure mode |
(config)#bridge 1 protocol ieee vlan-bridge | Create IEEE VLAN bridge 1. |
(config)#vlan 2 bridge 1 state enable | Create VLAN 2. |
(config)# ip dhcp snooping bridge 1 | Configure DHCP snooping for bridge 1 |
(config)# ip dhcp snooping information option bridge 1 | Configure DHCP snooping information option 82 |
(config)#cpu-queue vrrp-rip-dhcp rate 0 | Configure DHCP snooping ratelimit. Default value is 100 |
(config)# ip dhcp snooping vlan 2 bridge 1 | Configure DHCP snooping for vlan 2 for bridge 1 |
(config)# ip dhcp snooping verify mac-address bridge 1 | Configure DHCP snooping verify mac-address |
(config)#interface sa2 | Enter Interface Mode |
switchport | Configure the interface as Layer 2 |
bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#ip verify source dhcp-snooping-vlan | Configuring IP source guard at Interface level and configured on the interface which is connected to client side |
(config-if)#ip verify source access-group mode merge | Merge IPSG policy with other ACL |
(config-if)#exit | Exit interface mode |
(config)#interface xe2 | Enter Interface Mode |
(config-if)#switchport | Configure the interface as Layer 2 |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode access | Set the Layer2 interface as Access. (It can be Trunk mode also) |
(config-if)#switchport access vlan 2 | Set the default VLAN for the interface |
(config-if)#ip dhcp snooping trust | Configuring the interface as Trust. Basically this is configured on the interface which is connected to Server Side. |
(config-if)#exit | Exit interface mode. |
(config)#interface xe1 | Enter Interface Mode |
(config-if)#switchport | Configure the interface as Layer 2 |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode access | Set the Layer2 interface as Access. (It can be Trunk mode also) |
(config-if)#switchport access vlan 2 | Set the default VLAN for the interface |
(config-if)#static-channel-group 2 | Configure Static Channel lag on the interface |
(config-if)#exit | Exit interface mode |
(config)#ip dhcp snooping binding bridge 1 0011.1111.2222 2 ipv4 1.1.1.1 sa2 | Configure Ipv4 Static Entry For DHCP snooping with MAC address and Source Address for lag interface and vlan configured |
(config)#ip dhcp snooping binding bridge 1 0022.2222.3333 2 ipv6 3ffe::1 sa2 | Configure Ipv6 Static Entry For DHCP snooping with MAC address and Source Address for lag interface and vlan configured |
(config)#exit | Exit config mode |
#clear ip dhcp snooping binding bridge 1 | Clear DHCP binding tables which are learned dynamically |
Validation
Verify that DHCP snooping is enabled on the bridge with the static LAG interface:
#sh ip dhcp snooping bridge 1
Bridge Group : 1
DHCP snooping is : Enabled
DHCP snooping option82 is : Enabled
Verification of hwaddr field is : Enabled
DHCP snooping is configured on following VLANs : 2
DHCP snooping is operational on following VLANs : 2
DHCP snooping trust is configured on the following Interfaces
Interface Trusted
--------------- -------
Xe2 Yes
DHCP snooping IP Source Guard is configured on the following Interfaces
Interface Source Guard
--------------- ------------
sa2 Yes
Verify that static DHCP snooping or source guard entries are configured for the bridge with the LAG interface:
#sh ip dhcp snooping binding bridge 1
Total number of static IPV4 entries : 1
Total number of dynamic IPV4 entries : 0
Total number of static IPV6 entries : 1
Total number of dynamic IPV6 entries : 0
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- ------------------
0011.1111.2222 1.1.1.1 0 static 2 sa2
0022.2222.3333 3ffe::1 0 static 2 sa2