Single Hop BFD over IRB
Overview
The Single-hop Bidirectional Forwarding Detection (BFD) with BGP over EVPN-VXLAN IRB feature provides a lightweight, software-based failure detection mechanism for routed interfaces in virtualized data center networks. This feature enables BFD sessions over Integrated Routing and Bridging (IRB) interfaces without requiring hardware BFD support, ensuring compatibility with legacy or older routers that do not support BFD in hardware.
With this enhancement, BFD operates in the control plane, where software handles the transmission (TX), reception (RX), and state machine logic. This approach facilitates faster failure detection in environments using EVPN-VXLAN overlays with BGP routing over IRB interfaces.
This feature is ideal for networks with critical interoperability and control-plane flexibility, especially when upgrading or migrating from older hardware platforms.
Feature Characteristics
The Single-hop BFD with BGP over EVPN-VXLAN IRB feature includes the following characteristics:
• Software-based BFD operation: Introduces the CLI command bfd session software, enabling BFD to run in the control plane.
• Dedicated session state: Each BFD session maintains its own local discriminator, session state, and control-plane state machine.
• Interoperability: Supports BFD over IRB interfaces for routers that do not have hardware BFD capability.
• EVPN-VXLAN integration: Compatible with BGP routing over EVPN-VXLAN IRB deployments, improving failure detection across virtualized networks.
• No reliance on hardware: The software control plane manages the entire BFD session lifecycle, including packet processing.
Benefits
Implementing this feature provides the following advantages:
• Enhanced compatibility: Enables BFD deployment in networks with legacy routers that lack hardware BFD support.
• Improved resiliency: Offers faster failure detection and improved convergence in BGP EVPN-VXLAN environments.
• Flexible deployment: Facilitates BFD sessions over IRB interfaces without requiring hardware upgrades or dependencies.
• Simplified management: Reduces configuration complexity by allowing consistent BFD behavior across both new and existing platforms.
Limitations
• CPU-dependent scaling: The number of concurrent BFD sessions is limited by the CPU performance of the device, as all processing occurs in the control plane.
• Recommended interval: It is recommended to configure a minimum BFD interval of 250 ms to avoid excessive load on the control plane and ensure stable operation..
Configuration
Perform configuration steps for enabling Single-hop BFD with BGP over EVPN-VXLAN IRB, based on the configuration you provided. This includes enabling software-based BFD sessions over the IRB interface and configuring BFD integration with BGP in a VXLAN-EVPN environment.
Topology
The network topology includes various network elements such as routers, Customer Edge (CE) devices, Service Aggregator (SA) devices, and Provider Edge (PE) routers. The feature enables OSPF on the IRB interfaces, allowing for efficient routing and communication between network devices within the topology.
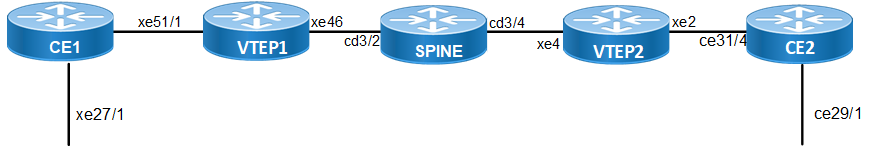 Single Hop BFD over EVPN-VXLAN IRB
Single Hop BFD over EVPN-VXLAN IRBPerform the following configurations to enable single-hop BFD with BGP over EVPN-VXLAN IRB.
1. Enable the BFD filter profile and set default timers globally to support BFD across the device.
VTEP1(config)# hardware-profile filter bfd-group enable
VTEP1(config)# bfd interval 50 minrx 50 multiplier 50
2. Configure the IRB interface to participate in L3 forwarding within a VRF and enable software-based BFD for failure detection.
VTEP1(config)#interface irb1601
VTEP1(config-irb-if)# ip vrf forwarding L3_VRF1
VTEP1(config-irb-if)# evpn irb-if-forwarding anycast-gateway-mac
VTEP1(config-irb-if)# ip address 12.0.0.12/24 anycast
VTEP1(config-irb-if)# ip address 71.10.0.2/24 secondary
VTEP1(config-irb-if)# ipv6 address 1100::1/48
VTEP1(config-irb-if)# ipv6 address 2a02:2488:2:2906::2/64 anycast
VTEP1(config-irb-if)# bfd interval 50 minrx 50 multiplier 50
VTEP1(config-if)# bfd session software
VTEP1(config-if)# exit
3. Define the VRF and associate it with a Layer 3 VNI to enable inter-subnet routing in the overlay network..
VTEP1(config)#ip vrf L3_VRF1
VTEP1(config-vrf)# rd 1.1.1.1:10
VTEP1(config-vrf)# route-target both 10:10
VTEP1(config-vrf)# l3vni 1000
VTEP1(config-vrf)# exit
4. Enable OSPF for both global and VRF instances to exchange routing information and support BFD for neighbor monitoring:
VTEP1(config)# router ospf 1
VTEP1(config-router)# ospf router-id 1.1.1.1
VTEP1(config-router)# bfd all-interfaces
VTEP1(config-router)# redistribute connected
VTEP1(config-router)# network 10.1.31.0/24 area 0.0.0.0
VTEP1(config-router)# exit
VTEP1(config)# router ospf 2 L3_VRF1
VTEP1(config-router)# ospf router-id 1.1.1.1
VTEP1(config-router)# bfd all-interfaces
VTEP1(config-router)# redistribute bgp
VTEP1(config-router)# network 71.10.0.0/24 area 0.0.0.0
VTEP1(config-router)# exit
5. Enable IS-IS routing for both underlay and VRF contexts and enable BFD for fast convergence.
VTEP1(config)# router isis 1
VTEP1(config-router)# is-type level-1-2
VTEP1(config-router)# metric-style wide
VTEP1(config-router)# dynamic-hostname
VTEP1(config-router)# bfd all-interfaces
VTEP1(config-router)# net 49.0000.0000.0001.00
VTEP1(config-router)# redistribute connected
VTEP1(config-router)# exit
VTEP1(config)# router isis 2 L3_VRF3
VTEP1(config-router)# is-type level-1-2
VTEP1(config-router)# metric-style wide
VTEP1(config-router)# dynamic-hostname
VTEP1(config-router)# bfd all-interfaces
VTEP1(config-router)# net 49.0000.0000.0465.00
VTEP1(config-router)# redistribute bgp
VTEP1(config-router)# exit
6. Bind interfaces to IS-IS.
VTEP1(config)# interface lo
VTEP1(config-if)# ip router isis 1
VTEP1(config-if)# exit
VTEP1(config)# interface xe46
VTEP1(config-if)# ip router isis 1
VTEP1(config-if)# exit
VTEP1(config)# interface irb1603
VTEP1(config-irb-if)# ip router isis 2
VTEP1(config-irb-if)# exit
7. Enable BGP for EVPN and VRF instances, configure peer relationships, and apply BFD to detect failures quickly.
VTEP1(config)# router bgp 100
VTEP1(config-router)# bgp router-id 1.1.1.1
VTEP1(config-router)# no bgp inbound-route-filter
VTEP1(config-router)# neighbor 3.3.3.3 remote-as 100
VTEP1(config-router)# neighbor 3.3.3.3 update-source lo
VTEP1(config-router)# neighbor 3.3.3.3 advertisement-interval 0
VTEP1(config-router)# address-family l2vpn evpn
VTEP1(config-router-af)# neighbor 3.3.3.3 activate
VTEP1(config-router-af)# exit-address-family
8. Configure BGP for each VRF:
L3_VRF1
VTEP1(config-router)# address-family ipv4 vrf L3_VRF1
VTEP1(config-router-af)# network 71.10.0.0/24
VTEP1(config-router-af)# redistribute connected
VTEP1(config-router-af)# redistribute ospf
VTEP1(config-router-af)# exit-address-family
L3_VRF2
VTEP1(config-router)# address-family ipv4 vrf L3_VRF2
VTEP1(config-router-af)# redistribute connected
VTEP1(config-router-af)# neighbor 91.10.0.1 remote-as 100
VTEP1(config-router-af)# neighbor 91.10.0.1 activate
VTEP1(config-router-af)# neighbor 91.10.0.1 update-source 91.10.0.2
VTEP1(config-router-af)# neighbor 91.10.0.1 fall-over bfd
VTEP1(config-router-af)# exit-address-family
L3_VRF3
VTEP1(config-router)# address-family ipv4 vrf L3_VRF3
VTEP1(config-router-af)# network 61.10.0.0/24
VTEP1(config-router-af)# redistribute connected
VTEP1(config-router-af)# redistribute isis
VTEP1(config-router-af)# exit-address-family
9. Enable VXLAN tunnel services and configure EVPN for Layer 2 and IRB services with anycast gateway MAC.
VTEP1(config)# nvo vxlan enable
VTEP1(config)# nvo vxlan irb
VTEP1(config)# evpn vxlan multihoming enable
VTEP1(config)# evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
VTEP1(config)# nvo vxlan vtep-ip-global 1.1.1.1
10. Configure L2VNI for each VRF:
L2 VRF1
VTEP1(config)# nvo vxlan id 1601 ingress-replication inner-vid-disabled
VTEP1(config-nvo)# vxlan host-reachability-protocol evpn-bgp L2_VRF1
VTEP1(config-nvo)# evpn irb1601
VTEP1(config-nvo)# vni-name VNI-1601
VTEP1(config-nvo)# exit
L2 VRF2
VTEP1(config)# nvo vxlan id 1602 ingress-replication inner-vid-disabled
VTEP1(config-nvo)# vxlan host-reachability-protocol evpn-bgp L2_VRF2
VTEP1(config-nvo)# evpn irb1602
VTEP1(config-nvo)# vni-name VNI-1602
VTEP1(config-nvo)# exit
L2 VRF3
VTEP1(config)# nvo vxlan id 1603 ingress-replication inner-vid-disabled
VTEP1(config-nvo)# vxlan host-reachability-protocol evpn-bgp L2_VRF3
VTEP1(config-nvo)# evpn irb1603
VTEP1(config-nvo)# vni-name VNI-1603
VTEP1(config-nvo)# exit
11. Assign each IRB to its corresponding VRF and configure IP addresses and BFD.
IRB1602
VTEP1(config)# interface irb1602
VTEP1(config-irb-if)# ip vrf forwarding L3_VRF2
VTEP1(config-irb-if)# ip address 11.0.11.11/24
VTEP1(config-irb-if)# ip address 91.10.0.2/24 secondary
VTEP1(config-irb-if)# ipv6 address 1200::1/48
VTEP1(config-irb-if)# bfd session software
VTEP1(config-irb-if)# exit
IRB1603
VTEP1(config)# interface irb1603
VTEP1(config-irb-if)# ip vrf forwarding L3_VRF3
VTEP1(config-irb-if)# evpn irb-if-forwarding anycast-gateway-mac
VTEP1(config-irb-if)# ip address 13.0.0.13/24 anycast
VTEP1(config-irb-if)# ip address 61.10.0.2/24 secondary
VTEP1(config-irb-if)# ipv6 address 1300::1/48
VTEP1(config-irb-if)# bfd session software
VTEP1(config-irb-if)# exit
12. Attach underlay interfaces for IS-IS, configure port-channel for multihoming, and set interface parameters.
VTEP1(config)# interface xe46
VTEP1(config-if)# load-interval 30
VTEP1(config-if)# ip address 10.1.31.1/24
VTEP1(config-if)# mtu 9000
VTEP1(config-if)# ip router isis 1
VTEP1(config-if)# exit
VTEP1(config)# interface xe51/1
VTEP1(config-if)# channel-group 1 mode active
VTEP1(config-if)# exit
VTEP1(config)# interface po1
VTEP1(config-if)# switchport
VTEP1(config-if)# load-interval 30
VTEP1(config-if)# evpn multi-homed system-mac 0000.aaaa.bbbb
VTEP1(config-if)# exit
Configuration Snapshot
!
vlan database
vlan-reservation 4039-4094
vlan 100 bridge 1
!
nvo vxlan enable
!
nvo vxlan irb
!
evpn vxlan multihoming enable
!
mac vrf m1
rd 2.2.2.2:1
route-target both 10:10
!
ip vrf vxlan_l3
rd 2222:300
route-target both 300:300
l3vni 5053
!
evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
!
nvo vxlan vtep-ip-global 2.2.2.2
!
nvo vxlan id 100 ingress-replication inner-vid-disabled
vxlan host-reachability-protocol evpn-bgp m1
evpn irb200
!
interface po10
switchport
load-interval 30
evpn multi-homed system-mac 0000.1122.3344
!
interface ce10
ip address 46.1.1.2/24
mtu 7000
!
interface ce15
channel-group 10 mode active
!
interface ce17
description leaf2-leaf3
ip address 20.0.0.1/24
mtu 7000
!
interface irb200
ip vrf forwarding vxlan_l3
evpn irb-if-forwarding anycast-gateway-mac
ip address 50.1.1.1/24 anycast
ip address 200.2.2.2/24 secondary
mtu 9216
bfd session software
!
interface lo
ip address 127.0.0.1/8
ip address 2.2.2.2/32 secondary
ipv6 address ::1/128
!
exit
!
router ospf 1
ospf router-id 2.2.2.2
network 2.2.2.2/32 area 0.0.0.0
network 20.0.0.0/24 area 0.0.0.0
network 46.1.1.0/24 area 0.0.0.0
!
router bgp 1
bgp router-id 2.2.2.2
neighbor 1.1.1.1 remote-as 1
neighbor 3.3.3.3 remote-as 1
neighbor 1.1.1.1 update-source lo
neighbor 1.1.1.1 advertisement-interval 0
neighbor 3.3.3.3 update-source lo
neighbor 3.3.3.3 advertisement-interval 0
!
address-family ipv4 unicast
redistribute connected
exit-address-family
!
address-family l2vpn evpn
neighbor 1.1.1.1 activate
neighbor 3.3.3.3 activate
exit-address-family
!
address-family ipv4 vrf vxlan_l3
max-paths ibgp 2
redistribute connected
neighbor 200.2.2.10 remote-as 1
neighbor 200.2.2.10 activate
neighbor 200.2.2.10 update-source 200.2.2.2
neighbor 200.2.2.10 fall-over bfd
exit-address-family
!
exit
!
line console 0
exec-timeout 0
!
nvo vxlan access-if port-vlan po10 100
map vnid 100
!
!
end
Implementation Examples
A data center is using EVPN-VXLAN to provide Layer 2 and Layer 3 segmentation across a spine-leaf fabric. IRB interfaces are configured on leaf switches to enable routed communication between VLANs. BGP is used as the control protocol for EVPN route exchange.
Enable software-based Single-hop BFD using the CLI bfd session software under the IRB interface or BGP neighbor configuration. This allows BFD to run entirely in the control plane.
New CLI Commands
bfd session software parameter is added under bfd session command. For more info refer to the Bidirectional Forwarding Commands section in the Layer 3 Guide.
Validation
show bfd session vrf all
BFD process for VRF: (DEFAULT VRF)
=====================================================================================
Sess-Idx Remote-Disc Lower-Layer Sess-Type Sess-State UP-Time Interface Down-Reason Remote-Addr
Number of Sessions: 0
BFD process for VRF: vxlan_l3
=====================================================================================
Sess-Idx Remote-Disc Lower-Layer Sess-Type Sess-State UP-Time Interface Down-Reason Remote-Addr
2049 2060 IPv4 Single-Hop Up 00:23:16 irb200 NA 200.2.2.10/32
Number of Sessions: 1
Glossary
The following provides definitions for key terms used throughout this document.
Single Home VxLAN | This refers to a Virtual Extensible LAN (VxLAN) deployment where a single data center or network site is connected to a single external network (usually the internet) for connectivity. |
IRB | A networking feature that enables the integration of Layer 3 IP routing and Layer 2 MAC address bridging within the same interface, simplifying network management and resource utilization. |
OSPF | A dynamic and efficient link-state routing protocol used to determine the best path for data packets in an IP network. It is characterized by rapid convergence and adaptability, making it suitable for large and dynamic networks. |
ISIS | A routing protocol designed for scalability and stability in computer networks, commonly used in large Service Provider networks. It provides a robust framework for routing information exchange. |
Layer 3 Routing | Network routing operations at the Network Layer (Layer 3) of the OSI model, focusing on routing IP packets between different subnets or networks. |
Layer 2 Bridging | Network bridging operations at the Data Link Layer (Layer 2) of the OSI model, handling the forwarding of data frames based on MAC addresses within the same network segment. |
EVPN | Ethernet VPN, a technology that provides advanced and efficient methods for Layer 2 and Layer 3 services in Ethernet networks, often used in data centers and service provider environments. |