BFD Authentication
This chapter provides BFD authentication configuration examples.
Overview
Bidirectional Forwarding Detection (BFD) is a protocol intended to detect faults in the bidirectional path between two forwarding engines, including physical interfaces, sub-interfaces, and data link. It operates independently of media, data protocols, and routing protocols. A session will be created between links. When BFD links is hacked, the link may be falsely declared to be down, or falsely declared to be up. To overcome this type of situations, need to use authentication on BFD. Using this we can mitigate threats from attackers.
OcNOS supports the following authentication types:
• Simple password
• Meticulous-Keyed-SHA1
• Keyed-SHA1
Among these types, Meticulous-Keyed-SHA1 is the strongest one.
Authentication is optionally enabled on BFD sessions. By default, it is disabled and is configurable via CLI. When authentication is enabled, BFD packets will exchange with authentication section (based on the configured auth type). Receiving system will examine the authentication section of the packet; if it is successful then it will accept. Otherwise, it will discard.
Enabling BFD Authentication for Multihop for IPv4, Using Key-ID
In this example, the BFD Multihop session is configured between R1 and R3 using single key (using key-ID). Once the BFD session is up, the authentication is enabled on both the routers, with the authentication type as Keyed-SHA1. We can enable the authentication on BFD session using any one of the above mentioned authentication type, with the Identical authentication type on both side.
Note: BFD authentication is not supported for Single hop BFD session.
Topology
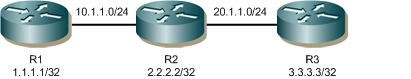
Basic Topology of Three Routers
Router 1 (R1)
R1#configure terminal | Enter the Configure mode. |
R1(config)#interface lo | Enter the Loopback Interface configuration mode. |
R1(config-if)#ip address 1.1.1.1/32 secondary | Assign IP address for interface |
R1(config-if)#commit | Commit the candidate configuration to the running configuration. |
R1(config-if)#exit | Exit from interface mode. |
R1(config)#interface xe9 | Enter Interface Mode. |
R1(config-if)#ip address 10.1.1.1/24 | Assign IP address for interface |
R1(config-if)#bfd session 10.1.1.1 20.1.1.2 multihop | Enabling BFD Multihop session |
R1(config-if)#commit | Commit the candidate configuration to the running configuration. |
R1(config-if)#exit | Exit from interface mode. |
R1(config)#router ospf 1 | Enter router OSPF mode |
R1(config-router)#redistribute connected | |
R1(config-router)#network 10.1.1.0/24 area 0 | Advertise the network to area 0 |
R1(config-if)#commit | Commit the candidate configuration to the running configuration. |
R1(config-router)#exit | Exit router OSPF mode |
R1(config)#bfd multihop-peer 20.1.1.2 auth type keyed-sha1 key-id 2 0 key ocnos | Enabling Authentication for Multihop session |
Router 2 (R2)
R2#configure terminal | Enter the Configure mode. |
R2(config)#interface lo | Enter the Loopback Interface configuration mode. |
R2(config-if)#ip address 2.2.2.2/32 secondary | Assign IP address for interface |
R2(config-if)#commit | Commit the candidate configuration to the running configuration. |
R2(config-if)#exit | Exit from interface mode. |
R2(config)#interface xe9 | Enter Interface Mode. |
R2(config-if)#ip address 10.1.1.2/24 | Assign IP address for interface |
R2(config-if)#exit | Exit from interface mode. |
R2(config)#interface xe2 | Enter Interface Mode. |
R2(config-if)#ip address 20.1.1.1/24 | Assign IP address for interface |
R2(config-if)#commit | Commit the candidate configuration to the running configuration. |
R2(config-if)#exit | Exit from interface mode. |
R2(config)#router ospf 1 | Enter router OSPF mode |
R2(config-router)#redistribute connected | |
R2(config-router)#network 10.1.1.0/24 area 0 | Advertise the network to area 0 |
R2(config-router)#network 20.1.1.0/24 area 0 | Advertise the network to area 0 |
R2(config-router)#commit | Commit the candidate configuration to the running configuration. |
R2(config-router)#exit | Exit router OSPF mode |
Router 3 (R3)
R3#configure terminal | Enter the Configure mode. |
R3(config)#interface lo | Enter the Loopback Interface configuration mode. |
R3(config-if)#ip address 3.3.3.3/32 secondary | Assign IP address for interface |
R3(config-if)#commit | Commit the candidate configuration to the running configuration. |
R3(config-if)#exit | Exit from interface mode. |
R3(config)#interface xe2 | Enter Interface Mode. |
R3(config-if)#ip address 20.1.1.2/24 | Assign IP address for interface |
R3(config-if)#bfd session 20.1.1.2 10.1.1.1 multihop | Enabling BFD Multihop session |
R3(config-if)#commit | Commit the candidate configuration to the running configuration. |
R3(config-if)#exit | Exit from interface mode. |
R3(config)#router ospf 1 | Enter router OSPF mode |
R3(config-router)#redistribute connected | |
R3(config-router)#network 20.1.1.0/24 area 0 | Advertise the network to area 0 |
R3(config-router)#exit | Exit router OSPF mode |
R3(config)#bfd multihop-peer 10.1.1.1 auth type keyed-sha1 key-id 2 0 key ocnos | Enabling Authentication for Multihop session |
R3(config)#commit | Commit the candidate configuration to the running configuration. |
Validation
Check Multihop session is up between R1 and R3 with authentication type configured.
R1#show ip ospf neighbor
Total number of full neighbors: 1
OSPF process 1 VRF(default):
Neighbor ID Pri State Dead Time Address Interface Instance ID
2.2.2.2 1 Full/DR 00:00:33 10.1.1.2 xe9 0
R1#sh bfd session
BFD process for VRF: (DEFAULT VRF)
=====================================================================================
Sess-Idx Remote-Disc Lower-Layer Sess-Type Sess-State UP-Time Interface Down-Reason Remote-Addr
1001 1001 IPv4 Multi-Hop Up 00:34:32 NA NA 20.1.1.2/32
Number of Sessions: 1
R1#sh bfd session detail
BFD process for VRF: (DEFAULT VRF)
====================================================================================
Session Interface Index : 0 Session Index : 1001
Lower Layer : IPv4 Version : 1
Session Type : Multihop Arbit Path Session State : Up
Local Discriminator : 1001 Local Address : 10.1.1.1/32
Remote Discriminator : 1001 Remote Address : 20.1.1.2/32
Local Port : 49152 Remote Port : 4784
Options :
Diagnostics : None
Timers in Milliseconds :
Min Tx: 250 Min Rx: 250 Multiplier: 3
Neg Tx: 250 Neg Rx: 250 Neg detect mult: 3
Min echo Tx: 1000 Min echo Rx: 1000 Neg echo intrvl: 0
Storage type : 2
Sess down time : 00:00:00
Sess Down Reason : NA
Bfd GTSM Disabled
Bfd Authentication Enabled
Authentication type : keyed-sha1
Authentication Key-id : 2
Counters values:
Pkt In : 00000000000000027907 Pkt Out : 00000000000000028347
Pkts Drop : 00000000000000000000 Auth Pkts Drop : 00000000000000000000
Echo Out : 00000000000000000000 IPv6 Echo Out : 00000000000000000000
IPv6 Pkt In : 00000000000000000000 IPv6 Pkt Out : 00000000000000000000
UP Count : 12 UPTIME : 00:34:34
Protocol Client Info:
BFD-> Client ID: 28 Flags: 4
----------------------------------------------------------
Number of Sessions: 1
R3#show ip ospf neighbor
Total number of full neighbors: 1
OSPF process 1 VRF(default):
Neighbor ID Pri State Dead Time Address Interface Instance ID
2.2.2.2 1 Full/Backup 00:00:32 20.1.1.1 xe2 0
R3#sh bfd session
BFD process for VRF: (DEFAULT VRF)
=====================================================================================
Sess-Idx Remote-Disc Lower-Layer Sess-Type Sess-State UP-Time Interface Down-Reason Remote-Addr
1001 1001 IPv4 Multi-Hop Up 00:36:27 NA NA 10.1.1.1/32
Number of Sessions: 1
R3#sh bfd session detail
BFD process for VRF: (DEFAULT VRF)
====================================================================================
Session Interface Index : 0 Session Index : 1001
Lower Layer : IPv4 Version : 1
Session Type : Multihop Arbit Path Session State : Up
Local Discriminator : 1001 Local Address : 20.1.1.2/32
Remote Discriminator : 1001 Remote Address : 10.1.1.1/32
Local Port : 49152 Remote Port : 4784
Options :
Diagnostics : None
Timers in Milliseconds :
Min Tx: 250 Min Rx: 250 Multiplier: 3
Neg Tx: 250 Neg Rx: 250 Neg detect mult: 3
Min echo Tx: 1000 Min echo Rx: 1000 Neg echo intrvl: 0
Storage type : 2
Sess down time : 00:00:00
Sess Down Reason : NA
Bfd GTSM Disabled
Bfd Authentication Enabled
Authentication type : keyed-sha1
Authentication Key-id : 2
Counters values:
Pkt In : 00000000000000028428 Pkt Out : 00000000000000028715
Pkts Drop : 00000000000000000000 Auth Pkts Drop : 00000000000000000000
Echo Out : 00000000000000000000 IPv6 Echo Out : 00000000000000000000
IPv6 Pkt In : 00000000000000000000 IPv6 Pkt Out : 00000000000000000000
UP Count : 12 UPTIME : 00:36:29
Protocol Client Info:
BFD-> Client ID: 28 Flags: 4
----------------------------------------------------------
Number of Sessions: 1