Access Control Lists Configurations
This chapter contains a complete example of access control list (ACL) configuration.
Overview
An Access Control List is a list of Access Control Entries (ACE). Each ACE in ACL specifies the access rights allowed or denied.
Each packet that arrives at the device is compared to each ACE in each ACL in the order they are defined. The device continues to look until it has a match. If no match is found and the device reaches the end of the list, the packet is denied. For this reason, place the most frequently occurring specifications at the top of the list.
The device stops checking the specifications after a match occurs.
Note: If there is no match, the packet is dropped (implicit deny). Therefore, an ACL intended to deny a few selected packets should have at least one permit filter of lower priority; otherwise, all traffic is dropped because of the default implicit deny filter.
Topology
.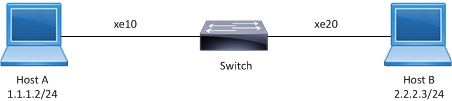

ACL sample topology
IPv4 ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list T1 | Create an IP access list named T1. |
(config-ip-acl)#deny any host 1.1.1.1 any | Create an access rule to deny IP packets with source address 1.1.1.1. |
(config-ip-acl)#permit any host 1.1.1.1/24 any | Create an access rule to permit IP packets with source address 1.1.1.1. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 1.1.1.3/24 | Assign an IP address. |
(config-if)#ip access-group T1 in | Apply access group T1 for inbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IP packets reach interface xe10 with source address 1.1.1.1, then the match count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists T1
IP access list T1
10 deny any host 1.1.1.1 any [match=200]
20 permit any 1.1.1.1/24 any
default deny-all
When inbound IP packets reach interface xe10 with a source address in the range from 1.1.1.1 to 1.1.1.254, then the match count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists T1
IP access list T1
10 deny any host 1.1.1.1 any
20 permit any 1.1.1.1/24 any [match=2000]
default deny-all
Note: Use the command clear ip access-list counters to clear the statistics of all ACLs or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
ICMP ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list icmp-acl-01 | Create an IP access list named icmp-acl-01. |
(config-ip-acl)#10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 f | Create an access rule with sequence number 10 to deny ICMP packets from a specific source towards a specific destination with a DSCP value of af11. Note: The sequence number is optional. |
(configip-acl)#20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash | Create an access rule with sequence number 20 to permit ICMP packets from a specific source towards a specific destination with precedence as flash. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 1.1.1.3/24 | Assign an IP address. |
(config-if)#ip access-group icmp-acl-01 in | Apply access group icmp-acl-01 for inbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IP packets reach interface xe10 with source address 1.1.1.X, destination address 2.2.2.X, DSCP value af11, and are fragmented, then the count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists icmp-acl-01
IP access-list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 [match=200]
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
When inbound IP packets reach interface xe10 with source address as 1.1.1.X, destination address 2.2.2.X, and precedence value flash, then the count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists icmp-acl-01
IP access-list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash [match=200]
default deny-all
Note: Use the command clear ip access-list counters to clear statistics of all ACLs configured or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
Access List Entry Sequence Numbering
You can change the sequence numbers of rules in an access list.
Note: Re-sequencing an ACL attached to a management interface clears the ACL counters associated to it.
#configure terminal | Enter configure mode. |
(config)#ip access-list icmp-acl-01 | Enter access list mode for ACL icmp-acl-01. |
(config-ip-acl)#resequence 100 200 | Re-sequence the access list, starting with sequence number 100 and incrementing by 200. |
(config-ip-acl)#1000 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 | Re-sequencing specific access rule 100 with sequence number 1000 |
(config-ip-acl)#exit | Exit access list mode. |
Validation
Before re-sequencing:
#show access-lists icmp-acl-01
IP access list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
After re-sequencing the access list, starting with sequence number 100 and incrementing by 200
#show access-lists icmp-acl-01
IP access list icmp-acl-01
100 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
300 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
After re-sequencing specific access rule 100 with sequence number 1000
#show access-lists icmp-acl-01
IP access list icmp-acl-01
300 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
1000 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
default deny-all
IPv6 ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ipv6 access-list ipv6-acl-01 | Create an IPv6 access list named as icmp-acl-01. |
(config-ipv6-acl)#11 deny ipipv6 any any flow-label 100 | Create access rule sequence number 11 to deny IPv4 encapsulated packets in IPv6 with any source address to any destination address with flow label 100. |
(config-ipv6-acl)#default permit-all | Update the default rule to permit all. |
(config-ipv6-acl)#exit | Exit access list mode |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ipv6 address 1:1::1:3/64 | Assign an IPv6 address. |
(config-if)#ipv6 access-group ipv6-acl-01 in | Apply access group ipv6-acl-01 for inbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IPv6 packets reach interface xe10 with IPv4 packets encapsulated with flow label 100, then count for access rule 11 increases equal to the number of packets sent.
#show ipv6 access-lists ipv6-acl-01
IPv6 access-list ipv6-acl-01
11 deny ipipv6 any any flow-label 100 [match=1000]
default permit all
For all other IPv6 packets, access rule 100 is invoked and the match counts increase equal to the number of packets sent.
#show ipv6 access-lists ipv6-acl-01
IPv6 access-list ipv6-acl-01
11 deny ipipv6 any any flow-label 100
default permit-all [match=2000]
Note: Use the command clear ipv6 access-list counters to clear statistics of all IPv6 ACLs configured or clear ipv6 access-list <ipv6 access-list name> counters to clear statistics of the particular IPv6 ACL.
MAC ACL Configuration
#configure terminal | Enter configure mode. |
(config)#mac access-list mac-acl-01 | Create a MAC access list named mac-acl-01. |
(config-mac-acl)#22 permit host 0000.0011.1212 host 0000.1100.2222 vlan 2 | Create an access rule with sequence number 22 to permit packets from a host with a specific MAC towards a host with a specific MAC with VLAN 2. |
(config-mac-acl)#exit | Exit access list mode. |
(config)#bridge 1 protocol rstp vlan-bridge | Create a VLAN-aware RSTP bridge. |
(config)#vlan 2 bridge 1 state enable | Create VLAN 2. |
(config)#interface xe10 | Enter interface mode. |
(config-if)#switchport | Configure the interface as Layer 2. |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode trunk | Set the switching characteristics of this interface to trunk mode. |
(config-if)#switchport trunk allowed vlan all | Enable all VLAN identifiers on this interface. |
(config-if)#mac access-group mac-acl-01 in | Applies the MAC access list mac-acl-01 to ingress traffic. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound packets reach interface xe10 with the specific source and destination MAC with the VLAN as 2, then the count for access rule 22 increases equal to the number of packets sent.
#show mac access-lists
MAC access list mac-acl-01
22 permit mac host 0000.0011.1212 host 0000.1100.2222 vlan 2 [match=3000]
default deny-all
For all other packets, default rule is invoked and the match counts increases equal to the number of packets sent.
#show mac access-lists mac-acl-01
MAC access list mac-acl-01
22 permit mac host 0000.0011.1212 host 0000.1100.2222 vlan 2
default deny-all [match=2000]
Note: As per the present design, ARP/ND packets will be filtered based on the source MAC address only (host mac address).
Note: Use the command clear mac access-list counters to clear statistics of all MAC ACLs or clear mac access-list <mac access-list name> counters to clear statistics of a particular MAC ACL.
Management ACL Overview
Management Port ACL can be used to provide basic level of security for accessing the management network. ACLs can also be used to decide which types of management traffic to be forwarded or blocked at the management port.
When configuring access list on a router or a switch, each access list needs to be identified by a unique name or a number. Each access list entry can have permit or deny actions. Each entry will be associated with a sequence number in the range of <1-268435453>. Lower the sequence number, higher the priority.
User should be able to configure the system to allow certain IP address for a protocol and don’t allow any other IP address matching for that protocol.
Note: If there is no match, the packet is dropped (implicit deny). Therefore, an ACL intended to deny a few selected packets should have at least one permit filter of lower priority; otherwise, all traffic is dropped because of the default implicit deny filter.
Topology
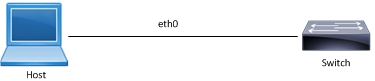
Management ACL Sample Topology
Management ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list mgmt | Create an IP access list named mgmt |
(config-ip-acl)#permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh | Create an access rule to permit TCP connection with source address 10.12.45.57 with destination address 10.12.29.49 on destination port equal to SSH. |
(config-ip-acl)#permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet | Create an access rule to permit TCP connection with source address 10.12.45.58 with Destination address 10.12.29.49 on destination port equal to Telnet. |
(config-ip-acl)#permit udp any host 10.12.29.49 eq snmp | Create an access rule to permit UDP packet with any source address with Destination address 10.12.29.49 on destination port equal to SNMP. |
(config-ip-acl)#permit udp any host 10.12.29.49 eq ntp | Create an access rule to permit UDP packet with any source address with Destination address 10.12.29.49 on destination port equal to NTP. |
(config-ip-acl)#permit udp host 10.12.29.49 any eq snmptrap | Create an access rule to permit UDP packet with source address 10.12.29.49 with any Destination address on destination port equal to SNMPTrap. |
(config-ip-acl)#permit tcp host 10.12.29.49 eq ssh host 10.12.45.57 | Create an access rule to permit TCP connection with source address 10.12.29.49 on source port equal to ssh with Destination address 10.12.45.57 . |
(config-ip-acl)#deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh | Create an access rule to deny TCP connection with source address 10.12.45.58 with Destination address 10.12.29.49 on destination port equal to SSH. |
(config-ip-acl)#deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet | Create an access rule to deny TCP connection with source address 10.12.45.57 with Destination address 10.12.29.49 on destination port equal to Telnet. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#interface eth0 | Enter interface mode of Management Interface. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 10.12.29.49/24 | Assign an IP address. |
(config-if)#ip access-group mgmt in | Apply access group mgmt for inbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When a TCP connection for Destination Port SSH reach interface eth0 with source address 10.12.45.57, then the match count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh [match=9]
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection for Destination Port Telnet reach interface eth0 with source address 10.12.45.58, then the match count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet [match=10]
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a UDP packet for Destination Port SNMP reach interface eth0 with any source address, then the match count for access rule 30 increases equal to the number of packets sent. Prior to this SNMP should be configured on Device (10.12.29.49).
Example:
snmp-server community SNMPTEST group network-admin vrf management
snmp-server host 10.12.6.86 traps version 2c SNMPTEST udp-port 162 vrf management
snmp-server enable snmp vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp [match=50]
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a UDP packet for Destination Port NTP reach interface eth0 with any source address, then the match count for access rule 40 increases equal to the number of packets sent. Prior to this NTP should be configured on Device (10.12.29.49).
Example:
ntp enable vrf management
ntp authenticate vrf management
ntp authentication-key 123 md5 swwx 7 vrf management
ntp trusted-key 123 vrf management
ntp server 10.12.45.36 vrf management
ntp server 10.12.16.16 prefer vrf management
ntp server 10.12.16.16 key 123 vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp [match=1]
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection request for Destination Port SSH reach interface eth0 with source address 10.12.45.58, this should deny the connection and the match count for access rule 70 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh [match=1]
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection request for Destination Port Telnet reach interface eth0 with source address 10.12.45.57, this should deny the connection and the match count for access rule 80 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet[match=1]
default deny-all
To enable SNMPTRAPS, apply the ACL outbound to the Management interface.
#configure terminal | Exit access list mode. |
(config)#interface eth0 | Enter interface mode of Management Interface. |
(config-if)#ip access-group mgmt out | Apply access group mgmt for outbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
When a UDP packet for Destination Port SNMPTrap sends out of interface eth0 with any Destination address, then the match count for access rule 50 increases equal to the number of packets received. Prior to this SNMPTrap should be configured on Device (10.12.29.49) to listen to port 162.
Example:
snmp-server community SNMPTEST group network-admin vrf management
snmp-server host 10.12.6.86 traps version 2c SNMPTEST udp-port 162 vrf management
snmp-server enable snmp vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap [match=5]
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When an ACL is applied on interface eth0 outbound and inbound together, then we must configure an ACL to establish a TCP connection between source 10.12.29.49 with source Port SSH to destination address 10.12.45.57. When a TCP connection is established on port SSH, then the match count for access rule 10 and 60 increases equal to the number of packets sent and received.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh [match=9]
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57[match=9]
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
Note: Use the command clear ip access-list counters to clear the statistics of all ACLs or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
#show access-lists
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
#show access-lists summary
IPV4 ACL mgmt
statistics enabled
Total ACEs Configured: 8
Configured on interfaces:
eth0 - ingress (Router ACL)
Active on interfaces:
eth0 - ingress (Router ACL)
#show access-lists expanded
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all [match=4]
ARP ACL Overview
ARP ACL can be used to permit or deny the ARP packets, based on the ARP request or response option configured.
Topology
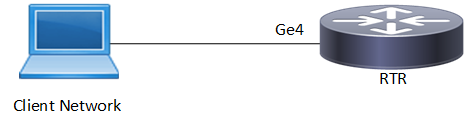
ARP ACL Sample Topology
ARP ACL Configuration
#configure terminal | Enter configure mode. |
(config)#interface ge4 | Enter interface mode. |
(config-if)#ip address 11.11.11.11/24 | Assign IPv4 address. |
(config-if)#exit | Exit access list mode. |
(config)#mac access-list mac1 | Enter mac access list mode. |
(config-mac-acl)#permit 0000.3ae0.456d 0000.0000.0000 any arp request | Create an access rule to permit specific ARP request. |
(config-mac-acl)#permit 0000.3ae0.456d 0000.0000.0000 any arp response | Create an access rule to permit specific ARP response. |
(config-mac-acl)#permit any any ipv4 | Create an access rule to permit any IPv4 packet. |
(config-mac-acl)#exit | Exit access list mode. |
(config)#interface ge4 | Enter interface mode. |
(config-if)#mac access-group mac1 in | Apply access group mac1 for inbound traffic to the interface. |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to assign IP address on IXIA and ping from IXIA.
#show mac access-lists
MAC access list mac1
10 permit host 0000.3AE0.456D any arp request [match=1]
20 permit host 0000.3AE0.456D any arp response [match=1]
30 permit any any ipv4 [match=1]
default deny-all
ACL OVER LOOPBACK
The loopback interface ACL is the feature to be used to provide this basic level security for the management applications accessible through In-band interfaces.
Note: Refer to command reference section for limitation, default behavior, and not supported features.
Topology
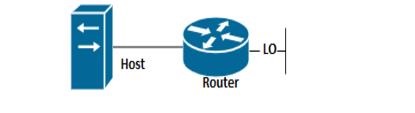
ACL Loopback Topology
Loopback ACL Configuration
#configure terminal | Enter configure mode. |
(config)#interface lo | Enter interface mode. |
(config-if)#ip address 3.3.3.3/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 4.4.4.4/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 5.5.5.5/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 6.6.6.6/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 7.7.7.7/32 secondary | Assign the IPv4 secondary address. |
(config-if)#exit | Exit interface mode. |
(config)#ip access-list loopback | Create loopback access list |
(config-ip-acl)#10 permit tcp any host 3.3.3.3 eq telnet | Permit telnet session from any source with specific destination. |
(config-ip-acl)#20 deny tcp any host 4.4.4.4 eq telnet | Deny telnet session from any source with specific destination. |
(config-ip-acl)#30 permit tcp any host 5.5.5.5 eq ssh | Permit ssh session from any source with specific destination. |
(config-ip-acl)#40 deny tcp any host 6.6.6.6 eq ssh | Deny ssh session from any source with specific destination. |
(config-ip-acl)#50 deny udp any host 6.6.6.6 eq snmp | Deny udp from any source with specific destination. |
(config-ip-acl)#60 deny udp any host 7.7.7.7 eq ntp | Deny udp from any source with specific destination. |
(config-ip-acl)#exit | Exit interface acl mode |
(config)#interface lo | Enter interface lo mode |
(config-if)#ip access-group loopback in | Associate loopback acl over lo interface |
(config-if)#exit | Exit interface mode |
(config)#exit | Exit config mode |
Validation
Use the commands below to validate ACL loopback.
OcNOS#sh access-lists
IP access list loopback
10 permit tcp any host 3.3.3.3 eq telnet [match=12]
20 deny tcp any host 4.4.4.4 eq telnet [match=12]
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh
50 deny udp any host 6.6.6.6 eq snmp [match=6]
60 deny udp any host 7.7.7.7 eq ntp
OcNOS#sh ip access-lists summary
IPV4 ACL loopback
statistics enabled
Total ACEs Configured: 6
Configured on interfaces:
lo - ingress (Router ACL)
Active on interfaces:
lo - ingress (Router ACL)
Configured on line vty:
OcNOS#sh running-config aclmgr
ip access-list loopback
10 permit tcp any host 3.3.3.3 eq telnet
20 deny tcp any host 4.4.4.4 eq telnet
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh
50 deny udp any host 6.6.6.6 eq snmp
60 deny udp any host 7.7.7.7 eq ntp
!
interface lo
ip access-group loopback in
!
ACL OVER VTY
When a Telnet/SSH/NetConf connection is established in the OcNOS, it associates the connection with a virtual terminal (VTY) line. The ACL over VTY feature provides security for management features associated with VTY.
Users can create Standard and Extended ACL rules and attach them to a virtual teletype (VTY) command line interface. These ACL rules are applied on both Management and Default virtual routing forwarding (VRFs).
OcNOS supports both IPv4 and IPv6 access lists for VTY lines, providing flexibility for network configurations.
Applying a standard ACL rule on a VTY line permits or denies only management access protocols such as SSH, Telnet, and SSH-Netconf protocols (port numbers 22,23,830)).
Extended ACL rules are applied as configured by the user, and it is not limited to management protocols only, unlike Standard ACLs.
When a user configures a rule with 'deny any any any' and attaches it to the VTY, it effectively blocks only the Telnet, SSH, and NetConf protocols on the control plane
For example, when a user configures a rule as below and attach them to VTY, If the deny ACL rule includes ’any’ value in protocol, only Telnet/SSH/SSH-NetConf protocols are denied.
ip access-list ssh-access
10 permit tcp 10.12.43.0/24 any eq ssh
20 deny any any any
Note: To deny any protocols other than Telnet/SSH/SSH-Netconf, create a deny rule with the specific protocol access on VTY. For example: To deny OSPF protocol from all the source and destination address, apply the rule, 10 deny ospf any any.
In general, the VTY ACLs are more specific to management protocols. Hence, the Extended ACL “any” rule translation is enhanced to allow management protocols as follows:
• If the deny ACL rule includes any value in protocol, only Telnet/SSH/SSH-Netconf protocols are denied.
• The permit ACL rule is unchanged.
Note: Refer to command reference section for limitation, default behavior, and not supported features.
Topology
ACL VTY Topology
VTY ACL Configuration
#configure terminal | Enter configure mode. |
(config)#interface lo | Enter interface mode. |
(config-if)#ip address 3.3.3.3/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 4.4.4.4/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 5.5.5.5/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 6.6.6.6/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 7.7.7.7/32 secondary | Assign the IPv4 secondary address. |
(config-if)#exit | Exit interface mode. |
(config)#ip access-list vty | Create loopback access list |
(config-ip-acl)#10 permit tcp any host 3.3.3.3 eq telnet | Permit telnet session from any source with specific destination. |
(config-ip-acl)#20 deny tcp any host 4.4.4.4 eq telnet | Deny telnet session from any source with specific destination. |
(config-ip-acl)#30 permit tcp any host 5.5.5.5 eq ssh | Permit ssh session from any source with specific destination. |
(config-ip-acl)#40 deny tcp any host 6.6.6.6 eq ssh | Deny ssh session from any source with specific destination. |
(config-ip-acl)#50 deny udp any host 6.6.6.6 eq snmp | Deny udp from any source with specific destination. |
(config-ip-acl)#60 deny udp any host 7.7.7.7 eq ntp | Deny udp from any source with specific destination. |
(config-ip-acl)#exit | Exit interface acl mode |
(config)#line vty | Enter interface vty mode |
(config-all-line)#ip access-group vty in | Associate acl over |
(config-if)#end | Exit interface mode |
(config)#exit | Exit config mode |
Validation
OcNOS#sh access-lists
IP access list vty
10 permit tcp any host 3.3.3.3 eq telnet [match=53]
20 deny tcp any host 4.4.4.4 eq telnet
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh [match=4]
50 deny udp any host 6.6.6.6 eq snmp
60 deny udp any host 7.7.7.7 eq ntp
OcNOS#sh ip access-lists summary
IPV4 ACL vty
statistics enabled
Total ACEs Configured: 6
Configured on interfaces:
Active on interfaces:
Configured on line vty:
all vty lines - ingress
OcNOS#sh running-config ac
access-list aclmgr
OcNOS#sh running-config aclmgr
ip access-list vty
10 permit tcp any host 3.3.3.3 eq telnet
20 deny tcp any host 4.4.4.4 eq telnet
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh
50 deny udp any host 6.6.6.6 eq snmp
60 deny udp any host 7.7.7.7 eq ntp
!
line vty
ip access-group vty in
Timed ACL
The time range feature was introduced to be able to add a timing boundary for specified activities. The activity would start, end and repeat at the specific times set by the user. This time-range feature will enable creating "Timed ACLs". This will help service providers customize the internet data to customers based on time to increase the video traffic during weekends and reduce data traffic, restrict the internet traffic in school/college non-working hours etc.
Topology
Timed acl sample topology
Configuration with ipv4 Address
#configure terminal | Enter configure mode. |
(config)# time-range TIMER1 | Configure a timer |
(config-tr)#start-time 10:00 03 nov 2021 | Configure start time |
(config-tr)#end-time 18:00 03 nov 2021 | Configure end time |
(config-tr)#exit | Exit timer |
(config)# ip access-list ACL1 | Create ip access list |
(config-ip-acl)# deny icmp host 10.1.1.1 host 10.1.2.2 | Create an acl rule to deny icmp |
(config-ip-acl)#exit | Exit Acl mode |
(config)#hardware-profile filter egress-ipv4 enable | Hardware profile enable for the acl |
(config)#int xe15 | Enter into the interface mode |
(config-if)#ip access-group ACL1 out time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | To save the changes |
(config-if)#exit | Exit |
Configuration with ipv6 Address
(config)# ipv6 access-list ACL1v6 | Create ipv6 access list |
(config-ipv6-acl)# deny any any any | Create an acl rule to deny |
(config-ipv6-acl)#exit | Exit Acl mode |
(config)# hardware-profile filter ingress-ipv6 enable | Hardware profile enable for the acl |
(config)#int xe12 | Enter into the interface mode |
(config-if)# ipv6 access-group ACL1v6 in time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | To save the changes |
(config-if)#exit | Exit |
Configuration with mac
(config)# mac access-list ACL1mac | Create ip access list |
(config-mac-acl)# deny 0000.0000.0000 1111.2222.3333 0000.0000.0000 4444.5555.6666 | Create an acl rule to deny icmp |
(config-mac-acl)#exit | Exit Acl mode |
(config)# hardware-profile filter ingress-l2 enable | Hardware profile enable for the acl |
(config)#int xe13 | Enter into the interface mode |
(config-if)# mac access-group ACL1mac in time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | To save the changes |
(config-if)#exit | Exit |
Validation
#sh running-config in xe15
!
interface xe15
ip access-group ACL1 out time-range TIMER1
!
OcNOS#sh running-config in xe12
!
interface xe12
ipv6 access-group ACL1v6 in time-range TIMER1
!
OcNOS#sh running-config in xe13
!
interface xe13
mac access-group ACL1mac in time-range TIMER1
#sh time-range
=====================================
TR handler interval: 10 seconds
=====================================
TR entries: 1
Entry: 0
name: TIMER1
state: Pending
frequency: none
start time: Wed Nov 3 10:00:00 2021
end time: Wed Nov 3 18:00:00 2021
=====================================
RUNNING TR entries: 0
=====================================
COMPLETED TR entries: 0