Access Control Lists Configurations
This chapter contains a complete example of access control list (ACL) configuration.
Overview
An Access Control List is a list of Access Control Entries (ACE). Each ACE in ACL specifies the access rights allowed or denied.
Each packet that arrives at the device is compared to each ACE in each ACL in the order they are defined. The device continues to look until it has a match. If no match is found and the device reaches the end of the list, the packet is denied. For this reason, place the most frequently occurring specifications at the top of the list.
The device stops checking the specifications after a match occurs.
Note: If there is no match, the packet is dropped (implicit deny). Therefore, an ACL intended to deny a few selected packets should have at least one permit filter of lower priority; otherwise, all traffic is dropped because of the default implicit deny filter.
Topology
.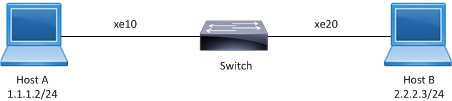

ACL sample topology
IPv4 ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list T1 | Create an IP access list named T1. |
(config-ip-acl)#deny any host 1.1.1.1 any | Create an access rule to deny IP packets with source address 1.1.1.1. |
(config-ip-acl)#permit any host 1.1.1.2 any | Create an access rule to permit IP packets with source address 1.1.1.2. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#hardware-profile filter ingress-ipv4 enable | Enable hardware profile for the ACL. |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 1.1.1.3/24 | Assign an IP address. |
(config-if)#ip access-group T1 in | Apply access group T1 for inbound traffic to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IP packets reach interface xe10 with source address 1.1.1.1, then the match count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists T1
IP access list T1
10 deny any host 1.1.1.1 any [match=200]
20 permit any 1.1.1.2 any
default deny-all
When inbound IP packets reach interface xe10 with a source address 1.1.1.2, then the match count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists T1
IP access list T1
10 deny any host 1.1.1.1 any
20 permit any 1.1.1.2 any [match=2000]
default deny-all
Note: Use the command clear ip access-list counters to clear the statistics of all ACLs or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
ICMP ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list icmp-acl-01 | Create an IP access list named icmp-acl-01. |
(config-ip-acl)#10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 | Create an access rule with sequence number 10 to deny ICMP packets from a specific source towards a specific destination with a DSCP value of af11. Note: The sequence number is optional. |
(configip-acl)#20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash | Create an access rule with sequence number 20 to permit ICMP packets from a specific source towards a specific destination with precedence as flash. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 1.1.1.3/24 | Assign an IP address. |
(config-if)#ip access-group icmp-acl-01 in | Apply access group icmp-acl-01 for inbound traffic to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IP packets reach interface xe10 with source address 1.1.1.X, destination address 2.2.2.X, DSCP value af11, and are fragmented, then the count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists icmp-acl-01
IP access-list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 [match=200]
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
When inbound IP packets reach interface xe10 with source address as 1.1.1.X, destination address 2.2.2.X, and precedence value flash, then the count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists icmp-acl-01
IP access-list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash [match=200]
default deny-all
Note: Use the command clear ip access-list counters to clear statistics of all ACLs configured or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
Access List Entry Sequence Numbering
You can change the sequence numbers of rules in an access list.
Note: Re-sequencing an ACL attached to a management interface clears the ACL counters associated to it.
#configure terminal | Enter configure mode. |
(config)#ip access-list icmp-acl-01 | Enter access list mode for ACL icmp-acl-01. |
(config-ip-acl)#resequence 100 200 | Re-sequence the access list, starting with sequence number 100 and incrementing by 200. |
(config-ip-acl)#1000 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 | Re-sequencing specific access rule 100 with sequence number 1000 |
(config-ip-acl)#exit | Exit access list mode. |
(config)#commit | Commit the candidate configuration to the running configuration |
Validation
Before re-sequencing:
#show access-lists icmp-acl-01
IP access list icmp-acl-01
10 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
20 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
After re-sequencing the access list, starting with sequence number 100 and incrementing by 200
#show access-lists icmp-acl-01
IP access list icmp-acl-01
100 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
300 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
default deny-all
After re-sequencing specific access rule 100 with sequence number 1000
#show access-lists icmp-acl-01
IP access list icmp-acl-01
300 permit icmp 1.1.1.1/24 2.2.2.2/24 precedence flash
1000 deny icmp 1.1.1.2/24 2.2.2.2/24 dscp af11 log
default deny-all
IPv6 ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ipv6 access-list ipv6-acl-01 | Create an IPv6 access list named as icmp-acl-01. |
(config-ipv6-acl)#11 deny ipipv6 any any | Create access rule sequence number 11 to deny IPv4 encapsulated packets in IPv6 with any source address to any destination address. |
(config-ipv6-acl)#default permit-all | Update the default rule to permit all. |
(config-ipv6-acl)#exit | Exit access list mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#interface xe10 | Enter interface mode. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ipv6 address 1:1::1:3/64 | Assign an IPv6 address. |
(config-if)#ipv6 access-group ipv6-acl-01 in | Apply access group ipv6-acl-01 for inbound traffic to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound IPv6 packets reach interface xe10 with IPv4, then count for access rule 11 increases equal to the number of packets sent.
#show ipv6 access-lists ipv6-acl-01
IPv6 access-list ipv6-acl-01
11 deny ipipv6 any any [match=1000]
default permit all
For all other IPv6 packets, access rule 100 is invoked and the match counts increase equal to the number of packets sent.
#show ipv6 access-lists ipv6-acl-01
IPv6 access-list ipv6-acl-01
11 deny ipipv6 any any
default permit-all [match=2000]
Note: Use the command clear ipv6 access-list counters to clear statistics of all IPv6 ACLs configured or clear ipv6 access-list <ipv6 access-list name> counters to clear statistics of the particular IPv6 ACL.
IPv6 ACL Configuration for 128-Bit Support
Configuration for Physical, PO, SA and MLAG Interfaces
Enable hardware-profile ingress-ipv6-ext:
(config)#hardware-profile filter ingress-ipv6-ext enable | Enable ingress IPv6 group for 128-bit address qualification on physical interfaces. |
(config)#commit | Commit the candidate configuration to the running configuration. |
(config)#ipv6 access-list test1 | Create an IPv6 access list named test1. |
(config-ipv6-acl)#permit any 2001::1/128 2002::1/128 | Create an access rule to permit any IPv6 packet from 2001::1/128 to 2002::1/128. |
(config-ipv6-acl)#commit | Commit the candidate configuration to the running configuration. |
(config)#interface xe1 | Enter interface mode. |
(config-if)#ipv6 access-group test1 in | Attach IPv6 access list test1 to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration. |
Validation
Use the commands below to verify the hardware-profile configurations.
#show hardware-profile filters
Note: Shared count is the calculated number from available resources.
Dedicated count provides allocated resource to the group.
If group shares the dedicated resource with other groups, then dedicated
count of group will reduce with every resource usage by other groups.
+-------------------------+---------+---------------+----------------------------+
| | Free | Used | Total Entries |
| Unit - TCAMS | Entries |---------------|----------------------------|
| | | % | Entries | Total | Dedicated | shared |
+-------------------------+---------+-----+---------+-------+-----------+--------+
0 INGRESS IPV6-ACL-EXT 1280 0 0 1280 0 1280
#
Use the commands below to verify the running configurations.
#show running-config ipv6 access-list
ipv6 access-list test1
10 permit any 2001::1/128 2002::1/128
!
#show running-config interface xe1
!
interface xe1
ipv6 access-group test1 in
!
#
Use the commands below to verify the match count.
#show ipv6 access-lists test1
IPv6 access list test1
10 permit any 2001::1/128 2002::1/128 [match=1000]
268435453 permit icmpv6 any any
default deny-all
#
Note: Use the command clear ipv6 access-list counters to clear statistics of all IPv6 ACLs configured or clear ipv6 access-list NAME counters to clear statistics of the particular IPv6 ACL.
Configuration for VLAN Interfaces and L3 Subinterfaces
Enable hardware-profile ingress-ipv6-ext-vlan.
(config)#hardware-profile filter ingress-ipv6-ext-vlan enable | Enable ingress IPv6 group for 128-bit address qualification on VLAN interfaces and subinterfaces. |
(config)#commit | Commit the candidate configuration to the running configuration. |
(config)#interface vlan1.20 | Enter interface mode. |
(config-if)#ipv6 access-group test1 in | Attach IPv6 access list test1 to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration. |
(config)#interface xe1.2 | Enter interface mode. |
(config-if)#ipv6 access-group test1 in | Attach IPv6 access list test1 to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration. |
Validation
Use the commands below to verify the hardware-profile configurations.
#show hardware-profile filters
Note: Shared count is the calculated number from available resources.
Dedicated count provides allocated resource to the group.
If group shares the dedicated resource with other groups, then dedicated
count of group will reduce with every resource usage by other groups.
+-------------------------+---------+---------------+----------------------------+
| | Free | Used | Total Entries |
| Unit - TCAMS | Entries |---------------|----------------------------|
| | | % | Entries | Total | Dedicated | shared |
+-------------------------+---------+-----+---------+-------+-----------+--------+
0 INGRESS IPV6-ACL-EXT-VLAN 1280 0 0 1280 0 1280
Use the commands below to verify the running configurations.
#show running-config ipv6 access-list
ipv6 access-list test1
10 permit any 2004::1/128 2005::1/128
!
#show running-config interface vlan1.20
!
interface vlan1.20
ipv6 access-group test1 in
#
#show running-config interface xe1.2
interface xe1.2
ipv6 access-group test1 in
!
Use the commands below to verify the match count.
#show ipv6 access-lists test1
IPv6 access list test1
10 permit any 2004::1/128 2005::1/128 [match=1000]
268435453 permit icmpv6 any any
default deny-all
Note: Use the command clear ipv6 access-list counters to clear statistics of all IPv6 ACLs configured or clear ipv6 access-list NAME counters to clear statistics of a particular IPv6 ACL.
MAC ACL Configuration
#configure terminal | Enter configure mode. |
(config)#mac access-list mac-acl-01 | Create a MAC access list named mac-acl-01. |
(config-mac-acl)#22 permit host 0000.0011.1212 host 0000.1100.2222 vlan 2 | Create an access rule with sequence number 22 to permit packets from a host with a specific MAC towards a host with a specific MAC with VLAN 2. |
(config-mac-acl)#exit | Exit access list mode. |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#bridge 1 protocol rstp vlan-bridge | Create a VLAN-aware RSTP bridge. |
(config)#vlan 2 bridge 1 state enable | Create VLAN 2. |
(config)#interface xe10 | Enter interface mode. |
(config-if)#switchport | Configure the interface as Layer 2. |
(config-if)#bridge-group 1 | Associate the interface with bridge group 1. |
(config-if)#switchport mode trunk | Set the switching characteristics of this interface to trunk mode. |
(config-if)#switchport trunk allowed vlan all | Enable all VLAN identifiers on this interface. |
(config-if)#mac access-group mac-acl-01 in | Applies the MAC access list mac-acl-01 to ingress traffic. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When inbound packets reach interface xe10 with the specific source and destination MAC with the VLAN as 2, then the count for access rule 22 increases equal to the number of packets sent.
#show mac access-lists
MAC access list mac-acl-01
22 permit mac host 0000.0011.1212 host 0000.1100.2222 vlan 2 [match=3000]
default deny-all
For all other packets, default rule is invoked and the match counts increases equal to the number of packets sent.
#show mac access-lists mac-acl-01
MAC access list mac-acl-01
22 permit mac host 0000.0011.1212 host 0000.1100.2222 vlan 2
default deny-all [match=2000]
Note: As per the present design, ARP/ND packets will be filtered based on the source MAC address only (host mac address).
Note: Use the command clear mac access-list counters to clear statistics of all MAC ACLs or clear mac access-list <mac access-list name> counters to clear statistics of a particular MAC ACL.
Management ACL Overview
Management Port ACL can be used to provide basic level of security for accessing the management network. ACLs can also be used to decide which types of management traffic to be forwarded or blocked at the management port.
When configuring access list on a router or a switch, each access list needs to be identified by a unique name or a number. Each access list entry can have permit or deny actions. Each entry will be associated with a sequence number in the range of <1-268435453>. Lower the sequence number, higher the priority.
User should be able to configure the system to allow certain IP address for a protocol and don’t allow any other IP address matching for that protocol.
Note: If there is no match, the packet is dropped (implicit deny). Therefore, an ACL intended to deny a few selected packets should have at least one permit filter of lower priority; otherwise, all traffic is dropped because of the default implicit deny filter.
Topology
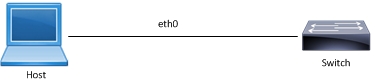
Management ACL Sample Topology
Management ACL Configuration
#configure terminal | Enter configure mode. |
(config)#ip access-list mgmt | Create an IP access list named mgmt |
(config-ip-acl)#permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh | Create an access rule to permit TCP connection with source address 10.12.45.57 with destination address 10.12.29.49 on destination port equal to SSH. |
(config-ip-acl)#permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet | Create an access rule to permit TCP connection with source address 10.12.45.58 with Destination address 10.12.29.49 on destination port equal to Telnet. |
(config-ip-acl)#permit udp any host 10.12.29.49 eq snmp | Create an access rule to permit UDP packet with any source address with Destination address 10.12.29.49 on destination port equal to SNMP. |
(config-ip-acl)#permit udp any host 10.12.29.49 eq ntp | Create an access rule to permit UDP packet with any source address with Destination address 10.12.29.49 on destination port equal to NTP. |
(config-ip-acl)#permit udp host 10.12.29.49 any eq snmptrap | Create an access rule to permit UDP packet with source address 10.12.29.49 with any Destination address on destination port equal to SNMPTrap. |
(config-ip-acl)#permit tcp host 10.12.29.49 eq ssh host 10.12.45.57 | Create an access rule to permit TCP connection with source address 10.12.29.49 on source port equal to ssh with Destination address 10.12.45.57 . |
(config-ip-acl)#deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh | Create an access rule to deny TCP connection with source address 10.12.45.58 with Destination address 10.12.29.49 on destination port equal to SSH. |
(config-ip-acl)#deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet | Create an access rule to deny TCP connection with source address 10.12.45.57 with Destination address 10.12.29.49 on destination port equal to Telnet. |
(config-ip-acl)#exit | Exit access list mode. |
(config)#hardware-profile filter egress-ipv4 enable | Enable hardware profile for the ACL. |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#interface eth0 | Enter interface mode of Management Interface. |
(config-if)#no switchport | Configure the interface as Layer 3. |
(config-if)#ip address 10.12.29.49/24 | Assign an IP address. |
(config-if)#ip access-group mgmt in | Apply access group mgmt for inbound traffic to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to verify the match count. When a TCP connection for Destination Port SSH reach interface eth0 with source address 10.12.45.57, then the match count for access rule 10 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh [match=9]
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection for Destination Port Telnet reach interface eth0 with source address 10.12.45.58, then the match count for access rule 20 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet [match=10]
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a UDP packet for Destination Port SNMP reach interface eth0 with any source address, then the match count for access rule 30 increases equal to the number of packets sent. Prior to this SNMP should be configured on Device (10.12.29.49).
Example:
snmp-server community SNMPTEST group network-admin vrf management
snmp-server host 10.12.6.86 traps version 2c SNMPTEST udp-port 162 vrf management
snmp-server enable snmp vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp [match=50]
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a UDP packet for Destination Port NTP reach interface eth0 with any source address, then the match count for access rule 40 increases equal to the number of packets sent. Prior to this NTP should be configured on Device (10.12.29.49).
Example:
ntp enable vrf management
ntp authenticate vrf management
ntp authentication-key 123 md5 swwx 7 vrf management
ntp trusted-key 123 vrf management
ntp server 10.12.45.36 vrf management
ntp server 10.12.16.16 prefer vrf management
ntp server 10.12.16.16 key 123 vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp [match=1]
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection request for Destination Port SSH reach interface eth0 with source address 10.12.45.58, this should deny the connection and the match count for access rule 70 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh [match=1]
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When a TCP connection request for Destination Port Telnet reach interface eth0 with source address 10.12.45.57, this should deny the connection and the match count for access rule 80 increases equal to the number of packets sent.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet[match=1]
default deny-all
To enable SNMPTRAPS, apply the ACL outbound to the Management interface.
#configure terminal | Exit access list mode. |
(config)#interface eth0 | Enter interface mode of Management Interface. |
(config-if)#ip access-group mgmt out | Apply access group mgmt for outbound traffic to the interface. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#end | Exit interface and configure mode. |
When a UDP packet for Destination Port SNMPTrap sends out of interface eth0 with any Destination address, then the match count for access rule 50 increases equal to the number of packets received. Prior to this SNMPTrap should be configured on Device (10.12.29.49) to listen to port 162.
Example:
snmp-server community SNMPTEST group network-admin vrf management
snmp-server host 10.12.6.86 traps version 2c SNMPTEST udp-port 162 vrf management
snmp-server enable snmp vrf management
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap [match=5]
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
When an ACL is applied on interface eth0 outbound and inbound together, then we must configure an ACL to establish a TCP connection between source 10.12.29.49 with source Port SSH to destination address 10.12.45.57. When a TCP connection is established on port SSH, then the match count for access rule 10 and 60 increases equal to the number of packets sent and received.
#show ip access-lists mgmt
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh [match=9]
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57[match=9]
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all
Note: Use the command clear ip access-list counters to clear the statistics of all ACLs or clear ip access-list <access-list name> counters to clear statistics of a particular ACL.
#show access-lists
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
#show access-lists summary
IPV4 ACL mgmt
statistics enabled
Total ACEs Configured: 8
Configured on interfaces:
eth0 - ingress (Router ACL)
Active on interfaces:
eth0 - ingress (Router ACL)
#show access-lists expanded
IP access list mgmt
10 permit tcp host 10.12.45.57 host 10.12.29.49 eq ssh
20 permit tcp host 10.12.45.58 host 10.12.29.49 eq telnet
30 permit udp any host 10.12.29.49 eq snmp
40 permit udp any host 10.12.29.49 eq ntp
50 permit udp host 10.12.29.49 any eq snmptrap
60 permit tcp host 10.12.29.49 eq ssh host 10.12.45.57
70 deny tcp host 10.12.45.58 host 10.12.29.49 eq ssh
80 deny tcp host 10.12.45.57 host 10.12.29.49 eq telnet
default deny-all [match=4]
ARP ACL Overview
ARP ACL can be used to permit or deny the ARP packets, based on the ARP request or response option configured.
Topology
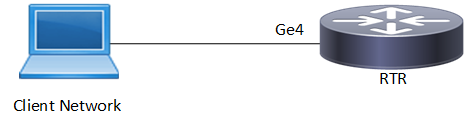
ARP ACL Sample Topology
ARP ACL Configuration
#configure terminal | Enter configure mode. |
(config)#interface ge4 | Enter interface mode |
(config-if)#ip address 11.11.11.11/24 | Assign IPv4 address. |
(config-if)#exit | Exit access list mode. |
(config)#commit | Commit the candidate configurations to the running configurations |
(config)#mac access-list m1 | Enter mac access list mode. |
(config-mac-acl)#permit any any vlan 6 | Create an access rule to permit any IPv6 packet |
(config-mac-acl)#permit 0000.0215.2151 0000.0000.0011 any vlan 3 | Create an access rule to permit specific ARP response. |
(config-mac-acl)#exit | Exit access list mode. |
(config)#commit | Commit the candidate configurations to the running configurations |
(config)#interface ge4 | Enter interface mode. |
(config-if)#mac access-group m1 in | Apply access group mac1 for inbound traffic to the interface. |
(config-if)#commit | Commit the candidate configurations to the running configurations |
(config-if)#end | Exit interface and configure mode. |
Validation
Use the commands below to assign IP address on IXIA and ping from IXIA.
#show mac access-lists
MAC access list mac1
10 permit host 0000.3AE0.456D any arp request [match=1]
20 permit host 0000.3AE0.456D any arp response [match=1]
30 permit any any ipv4 [match=1]
default deny-all
ACL over Loopback
The loopback interface ACL feature provides basic security for management applications accessible through In-band interfaces.
Note: Refer to the command reference section for limitations, default behavior, and unsupported features.
Topology
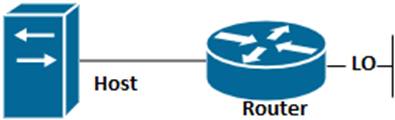
ACL Loopback Topology
#configure terminal | Enter configure mode. |
(config)#interface lo | Enter interface mode. |
(config-if)#ip address 3.3.3.3/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 4.4.4.4/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 5.5.5.5/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 6.6.6.6/32 secondary | Assign the IPv4 secondary address. |
(config-if)#ip address 7.7.7.7/32 secondary | Assign the IPv4 secondary address. |
(config-if)# exit | Exit interface mode. |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#ip access-list loopback | Create loopback access list |
(config-ip-acl)# 10 permit tcp any host 3.3.3.3 eq telnet | Permit telnet session from any source with specific destination. |
(config-ip-acl)# 20 deny tcp any host 4.4.4.4 eq telnet | Deny telnet session from any source with specific destination. |
(config-ip-acl)# 30 permit tcp any host 5.5.5.5 eq ssh | Permit ssh session from any source with specific destination. |
(config-ip-acl)# 40 deny tcp any host 6.6.6.6 eq ssh | Deny ssh session from any source with specific destination. |
(config-ip-acl)# 50 deny udp any host 6.6.6.6 eq snmp | Deny udp from any source with specific destination. |
(config-ip-acl)# 60 deny udp any host 7.7.7.7 eq ntp | Deny udp from any source with specific destination. |
(config-ip-acl)#exit | Exit interface acl mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#interface lo | Enter interface lo mode |
(config-if)#ip access-group loopback in | Associate loopback acl over lo interface |
(config-if)#exit | Exit interface mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#exit | Exit config mode |
Validation
#sh access-lists
IP access list loopback
10 permit tcp any host 3.3.3.3 eq telnet [match=12]
20 deny tcp any host 4.4.4.4 eq telnet [match=12]
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh
50 deny udp any host 6.6.6.6 eq snmp [match=6]
60 deny udp any host 7.7.7.7 eq ntp
#sh ip access-lists summary
IPV4 ACL loopback
statistics enabled
Total ACEs Configured: 6
Configured on interfaces:
lo - ingress (Router ACL)
Active on interfaces:
lo - ingress (Router ACL)
Configured on line vty:
#sh running-config aclmgr
ip access-list loopback
10 permit tcp any host 3.3.3.3 eq telnet
20 deny tcp any host 4.4.4.4 eq telnet
30 permit tcp any host 5.5.5.5 eq ssh
40 deny tcp any host 6.6.6.6 eq ssh
50 deny udp any host 6.6.6.6 eq snmp
60 deny udp any host 7.7.7.7 eq ntp
!
interface lo
ip access-group loopback in
!
ACL OVER Virtual Terminal (VTY)
When a Telnet/SSH/NetConf connection is established in the OcNOS, it associates the connection with a virtual terminal (VTY) line. The ACL over VTY feature provides security for management features associated with VTY.
Users can create Standard and Extended ACL rules and attach them to a virtual teletype (VTY) command line interface. These ACL rules are applied on both Management and Default virtual routing forwarding (VRFs).
OcNOS supports both IPv4 and IPv6 access lists for VTY lines, providing flexibility for network configurations.
Applying a standard ACL rule on a VTY line permits or denies only management access protocols such as SSH, Telnet, and SSH-Netconf protocols (port numbers 22,23,830)).
Extended ACL rules are applied as configured by the user, and it is not limited to management protocols only, unlike Standard ACLs.
When a user configures a rule with 'deny any any any' and attaches it to the VTY, it effectively blocks only the Telnet, SSH, and NetConf protocols on the control plane
For example, when a user configures a rule as below and attach them to VTY, If the deny ACL rule includes ’any’ value in protocol, only Telnet/SSH/SSH-NetConf protocols are denied.
ip access-list ssh-access
10 permit tcp 10.12.43.0/24 any eq ssh
20 deny any any any
Note: To deny any protocols other than Telnet/SSH/SSH-Netconf, create a deny rule with the specific protocol access on VTY. For example: To deny OSPF protocol from all the source and destination address, apply the rule, 10 deny ospf any any.
In general, the VTY ACLs are more specific to management protocols. Hence, the Extended ACL “any” rule translation is enhanced to allow management protocols as follows:
• If the deny ACL rule includes any value in protocol, only Telnet/SSH/SSH-Netconf protocols are denied.
• The permit ACL rule is unchanged. v
Note: Refer to the command reference section for limitations, default behavior, and unsupported features.
Topology
ACL VTY Topology
VTY ACL Configuration
#configure terminal | Enter configure mode. |
(config)#interface lo | Enter interface mode. |
(config-if)#ip address 3.3.3.3/32 secondary | Assign the IPv4 secondary address. |
(config-if)# exit | Exit interface mode. |
(config)#ip access-list vty | Create loopback access list |
(config-ip-acl)# 10 permit tcp any host 3.3.3.3 eq telnet | Permit telnet session from any source with specific destination. |
(config-ip-acl)#exit | Exit interface acl mode |
(config)#line vty | Enter interface vty mode |
(config-all-line)#ip access-group vty in | Associate acl over |
(config-if)#exit | Exit interface mode |
(config)#exit | Exit config mode |
Validation
OcNOS#sh access-lists
IP access list vty
10 permit tcp any host 3.3.3.3 eq telnet
OcNOS#sh ip access-lists summary
IPV4 ACL vty
statistics enabled
Total ACEs Configured: 1
Configured on interfaces:
Active on interfaces:
Configured on line vty:
all vty lines - ingress
OcNOS#sh running-config access-list
ip access-list vty
10 permit tcp any host 3.3.3.3 eq telnet
!
line vty
ip access-group vty in
Implementation Examples
OcNOS#show running-config aclmgr
ip access-list ssh-access
10 permit tcp 10.12.43.0/24 any eq ssh
20 deny tcp 10.12.33.0/24 any eq 6513
30 deny any 10.12.34.0/24 any
40 deny any any any
!
line vty
ip access-group ssh-access in
#####iptables o/p######
root@OcNOS:~# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 10.12.43.0/24 anywhere tcp dpt:ssh
DROP tcp -- 10.12.33.0/24 anywhere tcp dpt:tls_netconf
DROP tcp -- 10.12.34.0/24 anywhere multiport dports ssh,telnet,ssh_netconf
DROP tcp -- anywhere anywhere multiport dports ssh,telnet,ssh_netconf
Timed ACL Configuration
The time range feature was introduced to be able to add a timing boundary for specified activities. The activity would start, end and repeat at the specific times set by the user. This time-range feature will enable creating "Timed ACLs". This will help service providers to customize the internet data to customers based on time to increase the video traffic during weekends and reduce data traffic, restrict the internet traffic in school or college non-working hours etc.
Topology
Timed ACL sample topology
Configuration with IPv4 Address
#configure terminal | Enter configure mode. |
(config)#time-range TIMER1 | Configure a timer |
(config-tr)#start-time 10:00 03 nov 2021 | Configure start time |
(config-tr)#end-time 18:00 03 nov 2021 | Configure end time |
(config-tr)#exit | Exit timer |
(config)#ip access-list ACL1 | Create ip access list |
(config-ip-acl)# deny icmp host 10.1.1.1 host 10.1.2.2 | Create an acl rule to deny icmp |
(config-ip-acl)#exit | Exit Acl mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)#hardware-profile filter egress-ipv4 enable | Hardware profile enable for the acl |
(config)#int xe15 | Enter into the interface mode |
(config-if)#ip access-group ACL1 out time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#exit | Exit |
Configuration with IPv6 Address
(config)#ipv6 access-list ACL1v6 | Create ipv6 access list |
(config-ipv6-acl)# deny any any any | Create an acl rule to deny |
(config-ipv6-acl)#exit | Exit Acl mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)# hardware-profile filter ingress-ipv6 enable | Hardware profile enable for the acl |
(config)#int xe12 | Enter into the interface mode |
(config-if)# ipv6 access-group ACL1v6 in time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#exit | Exit |
Configuration with mac
(config)# mac access-list ACL1mac | Create ip access list |
(config-mac-acl)# deny 0000.0000.0000 1111.2222.3333 0000.0000.0000 4444.5555.6666 | Create an acl rule to deny icmp |
(config-mac-acl)#exit | Exit Acl mode |
(config)#commit | Commit the candidate configuration to the running configuration |
(config)# hardware-profile filter ingress-l2 enable | Hardware profile enable for the acl |
(config)#int xe13 | Enter into the interface mode |
(config-if)# mac access-group ACL1mac in time-range TIMER1 | Apply the acl along with the timer. |
(config-if)#commit | Commit the candidate configuration to the running configuration |
(config-if)#exit | Exit |
Validation
#sh running-config in xe15
!
interface xe15
ip access-group ACL1 out time-range TIMER1
!
#sh running-config in xe12
!
interface xe12
ipv6 access-group ACL1v6 in time-range TIMER1
!
#sh running-config in xe13
!
interface xe13
mac access-group ACL1mac in time-range TIMER1
#sh time-range
=====================================
TR handler interval: 10 seconds
=====================================
TR entries: 1
Entry: 0
name: TIMER1
state: Pending
frequency: none
start time: Wed Nov 3 10:00:00 2021
end time: Wed Nov 3 18:00:00 2021
=====================================
RUNNING TR entries: 0
=====================================
COMPLETED TR entries: 0
ACL on IRB Interface over MPLS EVPN
Applying ACLs to an Integrated Routing and Bridging (IRB) interface or switchport enables control over packet flow, whether ingress or egress the interface. This capability is essential for maintaining security, managing bandwidth, and ensuring effective routing and bridging.
Topology
In this topology, PE1 and PE2 routers have IRB interfaces configured. The IRB interfaces bridge VLAN traffic and route between VLANs, enabling communication between Layer 2 and Layer 3.
ACLs are applied on the IRB interfaces to filter traffic, ensuring only authorized traffic passes through. The P1 router acts as a transit router, forwarding traffic between PE1 and PE2. The P1 router provides core functionality but does not handle IRB interfaces directly.
This configuration ensures that while traffic flows across the network, ACL policies can be enforced at both PE1 and PE2 over the IRB interfaces, securing communication between VLANs and controlling access between external networks.
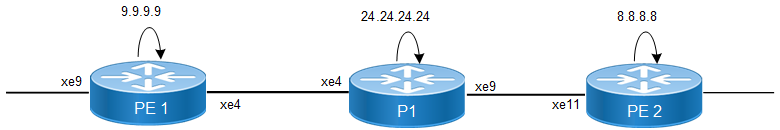
ACL on IRB sample topology
ACLs Configuration on IRB
Perform the following steps to enable EVPN MPLS on an IRB interface while applying ACLs to control ingress or egress traffic:
Note: The required configuration for ACL on IRB is added in the Configuration section, for the detailed configuration on IRB symmetric and asymmetric refer to the Configurations section in EVPN MPLS IRB Configuration.
1. Enable Hardware Profiles for both IPv4 and IPv6 traffic at the ingress and egress of the interface:
PE1(config)#hardware-profile filter ingress-ipv4-subif enable
PE1(config)#hardware-profile filter ingress-ipv6-ext-subif enable
PE1(config)#hardware-profile filter egress-ipv4-ext enable
PE1(config)#hardware-profile filter egress-ipv6 enable
PE1(config)#hardware-profile filter evpn-mpls-mh enable
PE1(config)#commit
2. Enable EVPN MPLS:
PE1(config)#evpn mpls enable
PE1(config)#evpn mpls irb
PE1(config)#evpn mpls multihoming enable # Only if multihoming is required
PE1(config)#commit
3. Configure an anycast MAC address for the gateway in a multihoming scenario, allowing multiple devices to share the same MAC address for redundancy:
PE1(config)#evpn irb-forwarding anycast-gateway-mac 0011.3333.5555 PE1(config)#commit
4. Define a MAC VRF for isolating MAC address routing within the EVPN framework:
PE1(config)#mac vrf vrfirb
PE1(config-vrf)# rd 9.9.9.9:2001
PE1(config-vrf)# route-target both 2001:2001
Note: Ensure to provide <RD value> with a value different from PE1’s RD of 9.9.9.9 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
5. Define an IP VRF for routing L3 traffic within the EVPN framework:
PE1(config)#ip vrf ip_vrfirb
PE1(config-vrf)# rd 9.9.9.9:200
PE1(config-vrf)# route-target both 200:200
PE1(config-vrf)# l3vni 20000
PE1(config-vrf)#commit
Note: Ensure to provide <rd value> with a value different from PE1’s RD of 9.9.9.9 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
6. Configure EVPN MPLS for host reachability and specify the IRB interface:
PE1(config-evpn-mpls)#evpn mpls id 200
PE1(config-evpn-mpls)#host-reachability-protocol evpn-bgp vrfirb
PE1(config-evpn-mpls)#evpn irb irb100
PE1(config-evpn-mpls)#commit
7. Configure a po interface for VLAN encapsulation and map it to the EVPN instance:
PE1(config)#interface po1000.200 switchport
PE1(config-if)# encapsulation dot1q 200
PE1(config-if)# rewrite pop
PE1(config-if)# load-interval 30
PE1(config-if)# access-if-evpn
PE1(config-acc-if-evpn)# map vpn-id 200
PE1(config-acc-if-evpn)#commit
8. Create ACL to filter outgoing traffic:
PE1(config)#ip access-list asy-egress
PE1(config-ip-acl)# 120 deny any host 70.70.1.2 80.80.1.0/24
PE1(config-ip-acl)#commit
9. Configure the IRB interface with IP addresses, associate it with the VRF, and apply the ACL:
PE1(config)#interface irb100
PE1(config-irb-if)# ip vrf forwarding ip_vrfirb
PE1(config-irb-if)# evpn irb-if-forwarding anycast-gateway-mac
PE1(config-irb-if)# ip address 80.80.1.1/24 anycast
PE1(config-irb-if)# ipv6 address 80:80::1/48 anycast
PE1(config-irb-if)# ip access-group asy-egress out
PE1(config-irb-if)#commit
Configuration Snapshot
PE1
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile filter ingress-ipv4-subif enable
hardware-profile filter ingress-ipv6-ext-subif enable
hardware-profile filter egress-ipv4-ext enable
hardware-profile filter evpn-mpls-mh enable
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
!
qos enable
!
hostname 7009-PE1
no ip domain-lookup
ip domain-lookup vrf management
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
lldp run
lldp tlv-select basic-mgmt system-name
lldp tlv-select basic-mgmt system-description
!
ip access-list asy-egress
120 deny any host 70.70.1.2 80.80.1.0/24
!
evpn mpls enable
!
evpn mpls irb
!
evpn mpls multihoming enable
!
ip vrf management
!
mac vrf vrfirb
rd 9.9.9.9:2001
route-target both 2001:2001
!
ip vrf ip_vrfirb
rd 9.9.9.9:200
route-target both 200:200
l3vni 20000
!
evpn irb-forwarding anycast-gateway-mac 0011.3333.5555
!
evpn mpls vtep-ip-global 9.9.9.9
!
evpn mpls id 200
host-reachability-protocol evpn-bgp vrfirb
evpn irb irb100
!
router ldp
router-id 9.9.9.9
targeted-peer ipv4 8.8.8.8
exit-targeted-peer-mode
transport-address ipv4 9.9.9.9
!
router rsvp
!
interface po1000
switchport
load-interval 30
mtu 9216
!
interface po1000.200 switchport
encapsulation dot1q 200
rewrite pop
load-interval 30
access-if-evpn
map vpn-id 200
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb100
ip vrf forwarding ip_vrfirb
evpn irb-if-forwarding anycast-gateway-mac
ip address 80.80.1.1/24 anycast
ip access-group asy-egress out
!
interface lo
ip address 127.0.0.1/8
ip address 9.9.9.9/32 secondary
ipv6 address ::1/128
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface xe3
!
interface xe4
description connected to 7024 P1
speed 10g
ip address 10.12.255.5/24
mtu 9216
label-switching
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
exit
!
interface xe9
channel-group 1000 mode active
!
router isis ISIS-IGP
is-type level-1
authentication mode md5 level-1
ignore-lsp-errors
lsp-gen-interval 5
spf-interval-exp level-1 50 2000
metric-style wide
mpls traffic-eng router-id 9.9.9.9
mpls traffic-eng level-1
capability cspf
dynamic-hostname
fast-reroute terminate-hold-on interval 10000
fast-reroute per-prefix level-1 proto ipv4 all
fast-reroute per-prefix remote-lfa level-1 proto ipv4 tunnel mpls-ldp
net 49.0001.0000.0000.0009.00
!
router bgp 65010
neighbor 8.8.8.8 remote-as 65010
neighbor 24.24.24.24 remote-as 65010
neighbor 8.8.8.8 update-source lo
neighbor 8.8.8.8 advertisement-interval 0
neighbor 24.24.24.24 update-source lo
neighbor 24.24.24.24 advertisement-interval 0
!
address-family l2vpn evpn
neighbor 8.8.8.8 activate
neighbor 24.24.24.24 activate
exit-address-family
!
address-family ipv4 vrf ip_vrfirb
redistribute connected
exit-address-family
!
exit
!
rsvp-trunk PE1-PE3 ipv4
to 8.8.8.8
!
!
end
PE2
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile filter ingress-ipv4-subif enable
hardware-profile filter ingress-ipv6-ext-subif enable
hardware-profile filter egress-ipv4-ext enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter evpn-mpls-mh enable
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
!
qos enable
!
hostname 7008-PE2
no ip domain-lookup
ip domain-lookup vrf management
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
lldp run
lldp tlv-select basic-mgmt system-name
lldp tlv-select basic-mgmt system-description
!
evpn mpls enable
!
evpn mpls irb
!
evpn mpls multihoming enable
!
ip vrf management
!
mac vrf vrfirb
rd 8.8.8.8:2000
route-target both 2000:2000
!
ip vrf ip_vrfirb
rd 8.8.8.8:200
route-target both 200:200
l3vni 20000
!
evpn mpls vtep-ip-global 8.8.8.8
!
evpn mpls id 101
host-reachability-protocol evpn-bgp vrfirb
evpn irb irb100
!
router ldp
router-id 8.8.8.8
targeted-peer ipv4 9.9.9.9
exit-targeted-peer-mode
transport-address ipv4 8.8.8.8
!
router rsvp
!
interface po2000
load-interval 30
mtu 9216
!
interface po2000.200 switchport
encapsulation dot1q 200
rewrite pop
load-interval 30
mtu 9216
access-if-evpn
map vpn-id 101
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb100
ip vrf forwarding ip_vrfirb
ip address 70.70.1.1/24
!
interface lo
ip address 127.0.0.1/8
ip address 8.8.8.8/32 secondary
ipv6 address ::1/128
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface xe11
description connected to 7024-P1
speed 10g
ip address 10.12.121.5/24
mtu 9216
label-switching
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
!
interface xe26
speed 10g
channel-group 2000 mode active
!
interface xe27
!
exit
!
router isis ISIS-IGP
is-type level-1
authentication mode md5 level-1
ignore-lsp-errors
lsp-gen-interval 5
spf-interval-exp level-1 50 2000
metric-style wide
mpls traffic-eng router-id 8.8.8.8
mpls traffic-eng level-1
capability cspf
dynamic-hostname
fast-reroute terminate-hold-on interval 10000
fast-reroute per-prefix level-1 proto ipv4 all
fast-reroute per-prefix remote-lfa level-1 proto ipv4 tunnel mpls-ldp
net 49.0001.0000.0000.0008.00
!
router bgp 65010
neighbor 9.9.9.9 remote-as 65010
neighbor 24.24.24.24 remote-as 65010
neighbor 9.9.9.9 update-source lo
neighbor 9.9.9.9 advertisement-interval 0
neighbor 24.24.24.24 update-source lo
neighbor 24.24.24.24 advertisement-interval 0
!
address-family l2vpn evpn
neighbor 9.9.9.9 activate
neighbor 24.24.24.24 activate
exit-address-family
!
address-family ipv4 vrf ip_vrfirb
redistribute connected
exit-address-family
!
exit
!
rsvp-trunk PE3-PE1 ipv4
to 9.9.9.9
!
!
end
P1
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
logging level nsm 4
logging level cmm 4
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile filter ingress-ipv4-subif enable
hardware-profile filter ingress-ipv6-ext-subif enable
hardware-profile filter egress-ipv4-ext enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter evpn-mpls-mh enable
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
!
qos enable
!
hostname 7024-P1
no ip domain-lookup
ip domain-lookup vrf management
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
lldp run
lldp tlv-select basic-mgmt port-description
lldp tlv-select basic-mgmt system-name
lldp tlv-select basic-mgmt system-capabilities
lldp tlv-select basic-mgmt system-description
lldp tlv-select basic-mgmt management-address
lldp notification-interval 1000
fault-management enable
!
evpn mpls enable
!
evpn mpls multihoming enable
!
ip vrf management
!
router ldp
!
router rsvp
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface ge25
!
interface lo
ip address 127.0.0.1/8
ip address 24.24.24.24/32 secondary
ipv6 address ::1/128
enable-ldp ipv4
enable-rsvp
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface xe4
description connected to 7009 PE1
speed 10g
ip address 10.12.255.4/24
mtu 9216
label-switching
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
!
interface xe9
description connected to 7008-PE2
speed 10g
ip address 10.12.121.4/24
mtu 9216
label-switching
ip router isis ISIS-IGP
enable-ldp ipv4
enable-rsvp
!
exit
!
router isis ISIS-IGP
is-type level-1
authentication mode md5 level-1
ignore-lsp-errors
lsp-gen-interval 5
spf-interval-exp level-1 50 2000
metric-style wide
mpls traffic-eng router-id 24.24.24.24
mpls traffic-eng level-1
capability cspf
dynamic-hostname
fast-reroute terminate-hold-on interval 10000
fast-reroute per-prefix level-1 proto ipv4 all
fast-reroute per-prefix remote-lfa level-1 proto ipv4 tunnel mpls-ldp
net 49.0001.0000.0000.0024.00
!
end
Validation
Verify that after applying ACL traffic is not egressing out:
7009-PE1#show interface counters rate mbps
+-------------------+--------------+-------------+--------------+-------------+
| Interface | Rx mbps | Rx pps | Tx mbps | Tx pps |
+-------------------+--------------+-------------+--------------+-------------+
xe4 6.53 6169 0.01 0
xe9 0.02 1 0.01 0
7009-PE1#show ip access-lists
IP access list asym-egress
120 deny any host 70.70.1.2 80.80.1.0 0.0.0.255 [match=220847]
default deny-all
Verify that the ACL rule is matching and counters are incremented accordingly:
7009-PE1#show ip access-lists
IP access list allow-1
IP access list asym-egress
120 deny any host 70.70.1.2 80.80.1.0 0.0.0.255 [match=242780]
7009-PE1#show ip access-lists
IP access list asym-egress
120 deny any host 70.70.1.2 80.80.1.0 0.0.0.255 [match=257475]
default deny-all
7009-PE1#show ip access-lists
IP access list asym-egress
120 deny any host 70.70.1.2 80.80.1.0 0.0.0.255 [match=272097]
default deny-all
ACL on IRB Interface over VXLAN EVPN
Applying ACLs to an Integrated Routing and Bridging (IRB) interface or switchport enables control over packet flow, whether ingress or egress the interface. This capability is essential for maintaining security, managing bandwidth, and ensuring effective routing and bridging.
Topology
In this topology, PE1 and PE2 routers have IRB interfaces configured. The IRB interfaces bridge VLAN traffic and route between VLANs, enabling communication between Layer 2 and Layer 3.
ACLs are applied on the IRB interfaces to filter traffic, ensuring only authorized traffic passes through. The P1 router acts as a transit router, forwarding traffic between PE1 and PE2. The P1 router provides core functionality but does not handle IRB interfaces directly.
This configuration ensures that while traffic flows across the network, ACL policies can be enforced at both PE1 and PE2 over the IRB interfaces, securing communication between VLANs and controlling access between external networks.
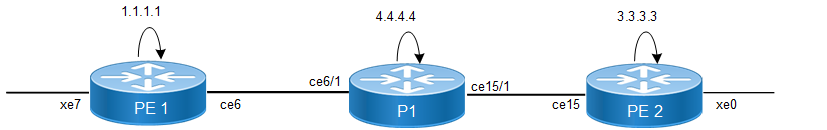
ACL on IRB sample topology
ACLs Configuration on IRB
Perform the following steps to enable EVPN VXLAN on an IRB interface while applying ACLs to control ingress or egress traffic:
Note: The required configuration for ACL on IRB is added in the Configuration section, for the detailed configuration on IRB symmetric and asymmetric refer to the Base Configuration - L2 VxLAN section in VxLAN-EVPN with IRB
1. Enable Hardware Profiles for both IPv4 and IPv6 traffic at the ingress and egress of the interface:
PE1(config)#hardware-profile filter ingress-ipv4-subif enable PE1(config)#hardware-profile filter ingress-ipv6-ext-subif enable PE1(config)#hardware-profile filter egress-ipv4-ext enable PE1(config)#hardware-profile filter egress-ipv6 enable
PE1(config)#hardware-profile filter vxlan enable
PE1(config)#hardware-profile filter vxlan-mh enable
PE1(config)#commit
2. Enable EVPN VXLAN:
PE1(config)#nvo vxlan enable
PE1(config)#nvo vxlan irb
PE1(config)#evpn vxlan multihoming enable # Only if multihoming is required PE1(config)#commit
3. Configure an anycast MAC address for the gateway in a multihoming scenario, allowing multiple devices to share the same MAC address for redundancy:
PE1(config)#evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
PE1(config)#commit
4. Define a MAC VRF for isolating MAC address routing within the EVPN framework:
PE1(config)#mac vrf vxlan_l2_elan_sh
PE1(config-vrf)#rd 1.1.1.1:101
PE1(config-vrf)#route-target both 101:101
Note: Ensure to provide <RD value> with a value different from PE1’s RD of 1.1.1.1 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
5. Define an IP VRF for routing L3 traffic within the EVPN framework:
PE1(config)#ip vrf vxlan_l3_elan_mhsh
PE1(config-vrf)#rd 1111:701
PE1(config-vrf)#route-target both 701:701
PE1(config-vrf)#l3vni 10050
PE1(config-vrf)#commit
Note: Ensure to provide <rd value> with a value different from PE1’s RD of 1.1.1.1 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
6. Configure EVPN VXLAN for host reachability and specify the IRB interface:
PE1(config)#nvo vxlan id 100 ingress-replication
PE1(config-nvo)# vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_mhsh
PE1(config-nvo)# evpn irb100
7. Configure a po interface for VLAN encapsulation and map it to the EVPN instance:
PE1(config)#interface xe7.100 switchport
PE1(config-if)# encapsulation dot1q 100
PE1(config-if)# rewrite pop
PE1(config-if)# access-if-evpn
PE1(config-acc-if-evpn)# map vpn-id 100
PE1(config-acc-if-evpn)#commit
8. Create ACL to filter outgoing traffic:
PE1(config)#
PE1(config)#ip access-list irb_100_nw
PE1(config-ip-acl)# 50 permit any 100.1.1.0/24 any
PE1(config-ip-acl)# 51 permit any 101.1.1.0/24 any
PE1(config-ip-acl)# default deny-all
PE1(config-ip-acl)# exit
PE1(config-ip-acl)#ipv6 access-list irb_100_v6
PE1(config-ipv6-acl)# 150 permit any 1001::/48 any
PE1(config-ipv6-acl)# default permit-all
PE1(config-ipv6-acl)#commit
9. Configure the IRB interface with IP addresses, associate it with the VRF, and apply the ACL:
PE1(config)#interface irb100
PE1(config-irb-if)# ip vrf forwarding vxlan_l3_elan_mhsh
PE1(config-irb-if)# evpn irb-if-forwarding anycast-gateway-mac
PE1(config-irb-if)# ip address 100.1.1.1/24 anycast
PE1(config-irb-if)# ip address 101.1.1.1/24 secondary anycast
PE1(config-irb-if)# ipv6 address 1001::1/48 anycast
PE1(config-irb-if)# ipv6 address 1002::1/48 anycast
PE1(config-irb-if)# ip access-group irb_100_nw in
PE1(config-irb-if)# ipv6 access-group irb_100_v6 in
PE1(config-irb-if)#commit
Configuration Snapshot
PE1
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
logging console 5
logging monitor 5
logging level nsm 5
logging level ospf 5
logging level hsl 5
logging level rib 5
logging level bgp 5
logging level pserv 5
logging level cmm 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
snmp-server enable traps ospf
snmp-server enable traps bgp
!
load-balance enable
load-balance ipv4 protocol-id src-dest-ipv4
load-balance ipv6 src-dest-ipv6
load-balance src-dest-l4port
hardware-profile filter ingress-ipv4-subif enable
hardware-profile filter ingress-ipv6-ext-subif enable
hardware-profile filter egress-ipv4-ext enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter vxlan enable
hardware-profile filter vxlan-mh enable
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
!
bfd interval 3 minrx 3 multiplier 3
!
qos enable
qos statistics
qos profile dscp-to-queue default
dscp 20 queue 4
!
hostname PE1
no ip domain-lookup
ip domain-lookup vrf management
ip name-server vrf management 10.12.3.24
bridge 1 protocol rstp vlan-bridge
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
username test role network-admin password encrypted
$1$bJoW4RH.$TPy.xPqFP4mOPALbPOX/b1
$1$bJoW4RH.$TPy.xPqFP4mOPALbPOX/b1
!
ip access-list irb_100_nw
50 permit any 100.1.1.0/24 any
51 permit any 101.1.1.0/24 any
default deny-all
!
ipv6 access-list irb_100_v6
150 permit any 1001::/48 any
default permit-all
!
vlan database
vlan 100 bridge 1
!
nvo vxlan enable
!
nvo vxlan irb
!
ip vrf management
!
mac vrf vxlan_l2_elan_mhsh
rd 1.1.1.1:101
route-target both 101:101
!
ip vrf vxlan_l3_elan_mhsh
rd 1111:701
route-target both 701:701
l3vni 10050
!
evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
!
nvo vxlan vtep-ip-global 1.1.1.1
!
nvo vxlan id 100 ingress-replication
vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_mhsh
evpn irb100
!
interface ce6
description network_to_spine1
load-interval 30
ip address 11.1.1.1/24
ip ospf cost 1
ip router isis 1
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb100
ip vrf forwarding vxlan_l3_elan_mhsh
evpn irb-if-forwarding anycast-gateway-mac
ip address 100.1.1.1/24 anycast
ip address 101.1.1.1/24 secondary anycast
ipv6 address 1001::1/48 anycast
ipv6 address 1002::1/48 anycast
ip access-group irb_100_nw in
ipv6 access-group irb_100_v6 in
!
interface lo
ip address 127.0.0.1/8
ip address 1.1.1.1/32 secondary
ipv6 address ::1/128
ip router isis 1
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface xe7
switchport
load-interval 30
!
interface xe7.100 switchport
encapsulation dot1q 100
rewrite pop
access-if-evpn
map vpn-id 100
!
exit
!
router ospf 1
ospf router-id 1.1.1.1
bfd all-interfaces
network 1.1.1.1/32 area 0.0.0.0
network 11.1.1.0/24 area 0.0.0.0
!
router bgp 1
bgp router-id 1.1.1.1
neighbor 3.3.3.3 remote-as 1
neighbor 3.3.3.3 update-source lo
!
address-family ipv4 unicast
max-paths ibgp 2
exit-address-family
!
address-family l2vpn evpn
neighbor 3.3.3.3 activate
exit-address-family
!
address-family ipv4 vrf vxlan_l3_elan_mhsh
max-paths ibgp 2
redistribute connected
exit-address-family
!
address-family ipv6 vrf vxlan_l3_elan_mhsh
max-paths ibgp 2
redistribute connected
exit-address-family
!
exit
!
line console 0
exec-timeout 0 0
line vty 0 16
exec-timeout 0 0
!
!
end
PE2
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
logging console 5
logging monitor 5
logging level nsm 5
logging level ospf 5
logging level hsl 5
logging level rib 5
logging level bgp 5
logging level pserv 5
logging level cmm 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
snmp-server enable traps ospf
snmp-server enable traps bgp
!
load-balance enable
load-balance ipv4 protocol-id src-dest-ipv4
load-balance ipv6 src-dest-ipv6
load-balance src-dest-l4port
hardware-profile filter ingress-ipv4-subif enable
hardware-profile filter ingress-ipv6-ext-subif enable
hardware-profile filter egress-ipv4-ext enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter vxlan enable
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
hardware-profile port-config mode3
!
bfd interval 3 minrx 3 multiplier 3
!
qos enable
qos statistics
qos profile dscp-to-queue default
dscp 20 queue 4
!
hostname PE2
port ce2 breakout 4X10g
no ip domain-lookup
ip domain-lookup vrf management
ip name-server vrf management 10.12.3.24
ip name-server vrf management 10.12.3.23
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
username test role network-admin password encrypted
$1$bJoWADy.$LH9n3Skfe1mL7qQ6NTCrS/
$1$bJoWADy.$LH9n3Skfe1mL7qQ6NTCrS/
lldp run
lldp tlv-select basic-mgmt port-description
lldp tlv-select basic-mgmt system-name
!
ip access-list irb_50_v4_ip
150 permit any host 50.1.1.2 any
151 permit any host 50.1.1.3 any
152 permit any host 50.1.1.4 any
default deny-all
!
ipv6 access-list irb_50_v6
150 permit any 5000::/48 any
default permit-all
!
nvo vxlan enable
!
nvo vxlan irb
!
ip vrf management
!
ip vrf vxlan_l3_elan_mhsh
rd 6666:701
route-target both 701:701
l3vni 10050
!
mac vrf vxlan_l2_elan_mhsh2
rd 6.6.6.6:50
route-target both 50:50
!
evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
!
nvo vxlan vtep-ip-global 3.3.3.3
!
nvo vxlan id 50 ingress-replication
vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_mhsh2
evpn irb50
!
interface ce15
description network_to_spine1
load-interval 30
ip address 15.1.1.1/24
ip ospf cost 1
ip router isis 1
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb50
ip vrf forwarding vxlan_l3_elan_mhsh
evpn irb-if-forwarding anycast-gateway-mac
ip address 50.1.1.1/24 anycast
ip address 51.1.1.1/24 secondary anycast
ipv6 address 5000::1/48 anycast
ipv6 address 5001::1/48 anycast
ip access-group irb_50_v4_ip in
ipv6 access-group irb_50_v6 in
!
interface lo
ip address 127.0.0.1/8
ip address 3.3.3.3/32 secondary
ipv6 address ::1/128
ip router isis 1
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface xe0
switchport
load-interval 30
!
interface xe0.50 switchport
encapsulation dot1q 50
rewrite pop
access-if-evpn
map vpn-id 50
!
interface xe2
switchport
!
interface xe3
!
exit
!
router ospf 1
ospf router-id 3.3.3.3
bfd all-interfaces
network 3.3.3.3/32 area 0.0.0.0
network 15.1.1.0/24 area 0.0.0.0
!
router bgp 1
bgp router-id 3.3.3.3
neighbor 1.1.1.1 remote-as 1
neighbor 1.1.1.1 update-source lo
!
address-family ipv4 unicast
max-paths ibgp 2
exit-address-family
!
address-family l2vpn evpn
neighbor 1.1.1.1 activate
exit-address-family
!
address-family ipv4 vrf vxlan_l3_elan_mhsh
max-paths ibgp 2
redistribute connected
exit-address-family
!
address-family ipv6 vrf vxlan_l3_elan_mhsh
max-paths ibgp 2
redistribute connected
exit-address-family
!
exit
!
line console 0
exec-timeout 0 0
line vty 0 16
exec-timeout 0 0
!
!
end
P1
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
logging console 5
logging monitor 5
logging level nsm 5
logging level ospf 5
logging level hsl 5
logging level rib 5
logging level bgp 5
logging level pserv 5
logging level cmm 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
qos enable
!
hostname P1
no ip domain-lookup
ip domain-lookup vrf management
ip name-server vrf management 10.12.3.24
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
lldp run
lldp tlv-select basic-mgmt port-description
lldp tlv-select basic-mgmt system-name
!
vlan database
vlan-reservation 4063-4094
!
ip vrf management
!
interface ce6/1
description network_to_vtep1
load-interval 30
ip address 11.1.1.2/24
ip ospf cost 10
ip router isis 1
!
interface ce14/4
!
interface ce15/1
description network_to_vtep3
load-interval 30
ip address 15.1.1.2/24
ip ospf cost 10
ip router isis 1
!
interface ce32/4
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface lo
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
exit
!
router ospf 1
ospf router-id 4.4.4.4
bfd all-interfaces
network 4.4.4.4/32 area 0.0.0.0
network 11.1.1.0/24 area 0.0.0.0
network 15.1.1.0/24 area 0.0.0.0
!
line console 0
exec-timeout 0 0
line vty 0 16
exec-timeout 0 0
!
!
end
Validation
Verify that after applying ACL traffic is not egressing out:
PE1#show interface counters rate mbps
+-------------------+--------------+-------------+--------------+-------------+
| Interface | Rx mbps | Rx pps | Tx mbps | Tx pps |
+-------------------+--------------+-------------+--------------+-------------+
ce6 312.62 224584 312.62 224583
xe7 229.97 224579 229.97 224579
xe7.100 198.36 225410 230.79 225377
PE1#
PE1#show access-lists
IP access list irb_100_nw
50 permit any 100.1.1.0/24 any [match=541906539]
51 permit any 101.1.1.0/24 any
default deny-all
IPv6 access list irb_100_v6
150 permit any 1001::/48 any [match=180636075]
268435453 permit icmpv6 any any [match=12]
default permit-all
Verify that the ACL rule is matching and counters are incremented accordingly:
PE1#show ip access-lists
IP access list irb_100_nw
50 permit any 100.1.1.0/24 any [match=563524977]
51 permit any 101.1.1.0/24 any
default deny-all
PE1#show ipv6 access-lists
IPv6 access list irb_100_v6
150 permit any 1001::/48 any [match=188010307]
268435453 permit icmpv6 any any [match=12]
default permit-all