Dynamic ARP Inspection
Overview
DAI (Dynamic ARP Inspection) is a security features that validates ARP packet in network by intercepting ARP packet and validating IP-to-MAC address binding learnt from DHCP SNOOP.
DAI (Dynamic ARP Inspection) is a security measures which allows user to intercept, log and discard ARP packets with invalid MAC address to IP address binding. Once the DAI feature is enabled on the system, ARP packets are re-directed to software and validated against the MAC to IP binding data base before getting forwarded. ARP coming on untrusted port is inspected, validated and forwarded/dropped appropriately.
Topology
.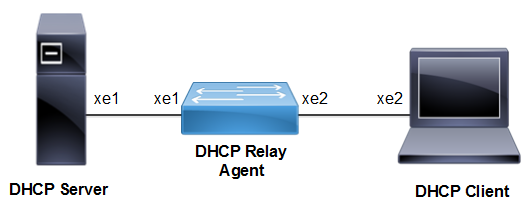

DAI Topology
Enable/Disable the Ingress DHCP-snoop TCAM group
#configure terminal | Enter Configure mode. |
(config)#hardware-profile filter dhcp-snoop enable | Enable the ingress DHCP-snoop TCAM group |
(config)#commit | Commit Candidate config to running-config |
(config)#hardware-profile filter dhcp-snoop disable | Disable the ingress DHCP-snoop TCAM group |
(config)#commit | Commit Candidate config to running-config |
Enable/Disable the Ingress DHCP-snoop-IPv6 TCAM group
#configure terminal | Enter Configure mode. |
(config)#hardware-profile filter dhcp-snoop-ipv6 enable | Enable the ingress DHCP-snoop-IPv6 TCAM group |
(config)#commit | Commit Candidate config to running-config |
(config)#hardware-profile filter dhcp-snoop-ipv6 disable | Disable the ingress DHCP-snoop-IPv6 TCAM group |
(config)#commit | Commit Candidate config to running-config |
Enable DHCP Snooping and DAI Globally
#configure terminal | Enter Configure mode. |
(config)#bridge 1 protocol mstp | Create MSTP or IEEE VLAN-bridge. |
(config)#ip dhcp snooping bridge 1 | Enable DHCP Snooping on the bridge |
(config)#ip dhcp snooping arp-inspection bridge 1 | Enable DAI on bridge |
(config)#commit | Commit Candidate config to running-config |
Enable DHCP Snooping and DAI on a VLAN
#configure terminal | Enter Configure mode. |
(config)#vlan 2 bridge 1 | Configure a VLAN for the bridge. |
(config)#ip dhcp snooping vlan 2 bridge 1 | Enable DHCP Snooping on the VLAN 2 |
(config)#ip dhcp snooping arp-inspection vlan 2 bridge 1 | Enable DAI on VLAN |
(config)#commit | Commit Candidate config to running-config |
Validation
OcNOS#show hardware-profile filters
Note: Shared count is the calculated number from available resources.
Dedicated count provides allocated resource to the group.
If group shares the dedicated resource with other groups, then dedicated
count of group will reduce with every resource usage by other groups.
+--------------------+---------+---------------+----------------------------+
| | Free | Used | Total Entries |
| Unit - TCAMS | Entries |---------------|----------------------------|
| | | % | Entries | Total | Dedicated | shared |
+--------------------+---------+-----+---------+-------+-----------+--------+
0 DHCP-SNOOP 5522 2 104 5626 1018 4608
0 DHCP-SNOOP-IPV6 5522 0 6 5528 920 4608
0 IPSG 3327 0 1 3328 1024 2304
0 IPSG-IPV6 3327 0 1 3328 1024 2304
Enable/Disable IP DHCP Snooping ARP-inspection Validate
Use this command to enable validation of the source-MAC, destination-MAC, or IP address field in the ARP packet payload.
Note: The IP address in a payload is validated for not being a broadcast address, a reserved zero IP address, and multicast address.
#configure terminal | Enter Configure mode. |
(config)#ip dhcp snooping arp-inspection validate src-mac bridge 1 | Enable SRC-MAC validate |
(config)#commit | Commit Candidate config to running-config |
(config)#no ip dhcp snooping arp-inspection validate src-mac bridge 1 | Disable SRC-MAC validate |
(config)#commit | Commit Candidate config to running-config |
(config)#ip dhcp snooping arp-inspection validate dst-mac bridge 1 | Enable DST-MAC validate |
(config)#commit | Commit Candidate config to running-config |
(config)#no ip dhcp snooping arp-inspection validate dst-mac bridge 1 | Disable DST-MAC validate |
(config)#commit | Commit Candidate config to running-config |
(config)#ip dhcp snooping arp-inspection validate ip bridge 1 | Enable IP validate |
(config)#commit | Commit Candidate config to running-config |
(config)#no ip dhcp snooping arp-inspection validate ip bridge 1 | Disable IP validate |
(config)#commit | Commit Candidate config to running-config |
Configuring the Ports Connected to DHCP Server and DHCP Client
#configure terminal | Enter Configure mode. |
(config)#interface xe1 | Specify the interface xe1 to be configured, and Enter interface mode |
(config-if)#switchport | Configure the interface as a switch port. |
(config-if)#bridge-group 1 | Associate the interface xe1 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port |
(config-if)#switchport access vlan 2 | Bind the interface VLAN 2 to the port |
(config-if)#exit | Exit interface mode. |
(config)#interface xe2 | Specify interface xe2 to be configured connected to server. |
(config-if)#switchport | Configure the interface as a switch port |
(config-if)#bridge-group 1 | Associate interface xe2 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port. |
(config-if)#switchport access vlan 2 | Bind the interface VLAN 2 to the port |
(config-if)#exit | Exit the config mode. |
(config)#commit | Commit Candidate config to running-config |
(config)#exit | Exit the config mode. |
Configuring Trusted and Un-trusted Ports
Usually the port connected to server is configured as trusted port and the ports connected to client is configured as un-trusted port.
In this example, xe2 is connected to the DHCP client and xe1 is connected to the DHCP server.
• Configure xe2 connected to DHCP client as un-trusted port.
• Configure xe1 connected to the DHCP server as trusted port.
#configure terminal | Enter Configure mode. |
(config)#interface xe1 | Specify the interface to be configured |
(config-if)#ip dhcp snooping trust | Enable the port as trusted. |
(config)#commit | Commit Candidate config to running-config |
(config)#interface xe2 | Specify the interface to be configured |
(config-if)#no ip dhcp snooping trust | Disable the port as trusted. |
(config-if)#exit | Exit interface mode |
(config)#commit | Commit Candidate config to running-config |
Validation
OcNOS#show ip dhcp snooping arp-inspection statistics bridge 1
bridge forwarded dai dropped
------ --------- -----------
1 0 10