In-band Management over Custom VRF
Overview
OcNOS currently supports system management protocols within the Default and Management Virtual Routing and Forwarding (VRF). However, this configuration is insufficient for customer deployments that require the ability to run these protocols in user-defined VRFs. This document outlines the requirements for expanding OcNOS to support system management protocols in custom VRFs.
Feature Characteristics
• Support for System Management Protocols in User-Defined VRFs: Provide the flexibility to run system management protocols over custom VRFs. In large-scale networks, deploying an out-of-band management network is not always practical, making in-band device management over user-defined VRFs necessary to handle the volume of management traffic.
• Supported Protocols: SSH, Telnet, TACACS, Syslog, SNMP, NETCONF, and gNMI will operate within user-defined VRFs. Simultaneous support for multiple VRFs for specific protocols, such as Syslog. Support for both default and customizable port values for each protocol.
• Multi-VRF Protocol Operations: Management protocols, including SSH and NETCONF, will allow simultaneous operations across multiple VRFs, providing enhanced flexibility in managing network devices.
• Service Traffic Segmentation: Management traffic, such as SNMP and Syslog, can be segmented across custom VRFs, allowing for more efficient traffic management and security.
Benefits
• Scalability and Flexibility: Enabling system management protocols to operate over custom VRFs allows for ease of managing service provider networks, especially in environments where out-of-band management is impractical.
• Protocol Customization: Support for both standard and customizable port values for management protocols provides greater flexibility, allowing customers to tailor the system management configuration to meet their specific network needs.
Configuration
These steps provide a standardized approach to configuring User-Defined VRF on PE routers.
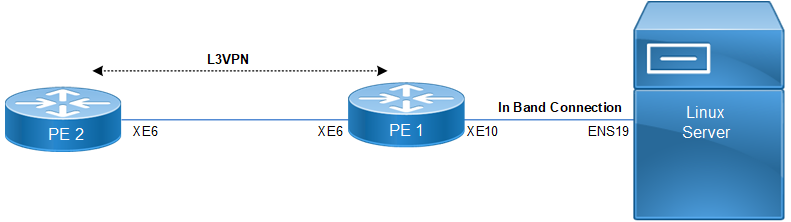
Topology
In this topology, the management traffic from the Linux Server is routed through a specific VRF that is isolated from the traffic on the L3VPN.
PE1 and PE2 are Provider Edge routers in the network. These routers are responsible for managing and routing the traffic between the local network and the wider service provider network.
Both PE routers are connected through L3VPN, which is used to segment and isolate traffic between the two routers over a shared infrastructure. Each customer or service can have its own isolated routing table (VRF).
In-Band Connection: The In-Band Connection shown between PE1 and the Linux Server means that both management and normal traffic flow over the same physical network links.
The in-band management traffic is directed over the custom VRF, ensuring it is separated from the service traffic, providing network isolation.
Custom VRF Feature: In this case, the custom VRF is applied to manage the traffic between the Linux Server and the network. This VRF allows traffic related to management tasks to remain separate from other traffic handled by the provider.
VRF helps ensure that different traffic types (such as syslog, or SSH sessions) remain isolated for security and performance reasons.
Multi-VRF Management: Using user-defined VRFs, run management services like Syslog, or SSH on separate VRFs, ensuring that management tasks are not mixed with customer or service traffic.
Custom VRF
Perform the following configuration steps for setting up a custom VRF with routing protocols like BGP, OSPF, and management protocols such as SSH. These can be applied to multiple Provider Edge (PE) routers, or other routers, with adjustments in interface names and IP addresses depending on the specific deployment.
The steps include defining VRFs, configuring interfaces, setting up routing protocols like OSPF and BGP, enabling management features (SSH), and ensuring MPLS support:
1. Enter configuration mode and define the VRF.
#configure terminal
(config)# ip vrf vrf1
(config)# rd 100:1
(config)# route-target both 10:10
(config)#exit
2. Assign the VRF to the relevant access and loopback interfaces, and configure both IPv4 or IPv6 addresses:
Access Interface Configuration:
#configure terminal
(config)# interface xe10
(config)# ip vrf forwarding vrf1
(config)# ip address 20.20.20.3/24
(config)# ipv6 address 2500::3/64
(config)#exit
Loopback Interface Configuration:
#configure terminal
(config)# interface lo.vrf1
(config)# ip vrf forwarding vrf1
(config)# ip address 172.16.1.10/24 secondary
(config)# ipv6 address 2000::10/64
(config)#exit
3. On interfaces facing the provider network, configure MPLS and enable LDP:
(config)# interface xe6
(config)# ip address 192.168.69.1/24
(config)# ipv6 address 1000::11/64
(config)# label-switching
(config)# enable-ldp ipv4
(config)#exit
4. Set up OSPF routing within the network, and ensure to advertise the necessary interfaces:
(config)# router ospf 100
(config)# network 1.1.1.1/32 area 0.0.0.0
(config)# network 192.168.69.0/24 area 0.0.0.0
(config)#commit
(config)#exit
#configure terminal
(config)# router ldp
(config)#exit
5. Configure BGP for both VPNv4 and VPNv6 address families:
#configure terminal
(config)# router bgp 1000
(config)# neighbor 2.2.2.2 remote-as 1000
(config)# neighbor 2.2.2.2 update-source 1.1.1.1
(config)# address-family vpnv4 unicast
(config)# neighbor 2.2.2.2 activate
(config)# exit-address-family
(config)# address-family ipv4 vrf vrf1
(config)# redistribute connected
(config)# exit-address-family
(config)# address-family vpnv6 unicast
(config)# neighbor 2.2.2.2 activate
(config)# exit-address-family
(config)# address-family ipv6 vrf vrf1
(config)# redistribute connected
(config)# exit-address-family
(config)#exit
6. Enable SSH (or respective protocols) for VRF Management:
#configure terminal
(config)# feature ssh vrf management
(config)# feature ssh vrf
(config)# feature ssh vrf vrf1
(config)#exit
(config)# ssh server port 10000 vrf management
(config)# ssh server port 10000
(config)# ssh server port 10000 vrf vrf1
(config)#exit
(config)# ssh login-attempts 2 vrf management
(config)# ssh login-attempts 2
(config)# ssh login-attempts 2 vrf vrf vrf1
(config)#exit
(config)# ssh server session-limit 10 vrf management
(config)# ssh server session-limit 10
(config)# ssh server session-limit 20 vrf vrf1
(config)#exit
(config)# ssh server algorithm encryption 3des-cbc vrf management
(config)# ssh server algorithm encryption 3des-cbc
(config)# ssh server algorithm encryption 3des-cbc vrf vrf1
(config)#exit
Configuration Snapshot:
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
no feature netconf-ssh
no feature netconf-tls
service password-encryption
!
logging console
logging monitor
logging cli
logging level all 7
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile statistics voq-full-color enable
hardware-profile statistics cfm-ccm enable
!
qos enable
!
no ip domain-lookup
ip domain-lookup vrf management
tfo Disable
errdisable cause stp-bpdu-guard
no feature telnet vrf management
no feature telnet
feature ssh vrf management
no feature ssh
feature ssh vrf vrf1
ssh server port 10000 vrf vrf1
ssh login-attempts 2 vrf vrf1
ssh server algorithm encryption 3des-cbc vrf vrf1
ssh server session-limit 20 vrf vrf1
feature dns relay
ip dns relay
ipv6 dns relay
feature ntp vrf management
ntp enable vrf management
lldp tlv-select basic-mgmt port-description
lldp tlv-select basic-mgmt system-name
lldp tlv-select basic-mgmt system-capabilities
lldp tlv-select basic-mgmt system-description
!
ip vrf management
!
ip vrf vrf1
rd 100:1
route-target both 10:10
!
router ldp
!
ip vrf forwarding management
ip address dhcp
!
interface lo
ip address 127.0.0.1/8
ip address 1.1.1.1/32 secondary
ipv6 address ::1/128
!
interface lo.management
ip vrf forwarding management
ip address 127.0.0.1/8
ipv6 address ::1/128
!
interface lo.vrf1
ip vrf forwarding vrf1
ip address 172.16.1.10/24 secondary
ipv6 address 2000::10/64
!
interface xe6
speed 10g
ip address 192.168.69.1/24
ipv6 address 1000::11/64
label-switching
enable-ldp ipv4
!
ip vrf forwarding vrf1
ip address 20.20.20.3/24
ipv6 address 2500::3/64
!
!
router ospf 100
network 1.1.1.1/32 area 0.0.0.0
network 192.168.69.0/24 area 0.0.0.0
!
router bgp 1000
neighbor 2.2.2.2 remote-as 1000
neighbor 2.2.2.2 update-source 1.1.1.1
!
address-family vpnv4 unicast
neighbor 2.2.2.2 activate
exit-address-family
!
address-family vpnv6 unicast
neighbor 2.2.2.2 activate
exit-address-family
!
address-family ipv4 vrf vrf1
redistribute connected
exit-address-family
!
address-family ipv6 vrf vrf1
redistribute connected
exit-address-family
!
exit
!
line console 0
exec-timeout 0 0
line vty 0
exec-timeout 0 0
!
Validation
Validate the VRF and SSH configurations to ensure they support the custom VRF functions as expected.
• Verify the VRF Configuration:
OcNOS#show running-config vrf vrf1
!
ip vrf vrf1
rd 100:1
route-target both 10:10
!
OcNOS#show running-config interface xe10
!
interface xe10
ip vrf forwarding vrf1
ip address 20.20.20.3/24
ipv6 address 2500::3/64
!
OcNOS#show running-config interface lo.vrf1
!
interface lo.vrf1
ip vrf forwarding vrf1
ip address 172.16.1.10/24 secondary
ipv6 address 2000::10/64
!
OcNOS#show running-config interface xe6
interface xe6
speed 10g
ip address 192.168.69.1/24
ipv6 address 1000::11/64
label-switching
enable-ldp ipv4
!
• Verify SSH configuration:
OcNOS#show running-config ssh server
feature ssh vrf management
no feature ssh
feature ssh vrf vrf1
ssh server port 10000 vrf vrf1
OcNOS#show ssh server
VRF MANAGEMENT:
ssh server enabled port: 22
authentication-retries: 3
VRF DEFAULT:
ssh server disabled port: 22
authentication-retries: 3
VRF vrf1:
ssh server enabled port: 10000
session-limit: 20
authentication-retries: 2
Implementation Examples
• L3VPN or EVPN Tunnel Support: In a service provider network, user-defined VRFs are configured on managed nodes, such as PE and Rout Reflector (RR) nodes. Management nodes connect to a PE node, enabling access to other PE or RR nodes through L3VPN or EVPN tunnels. This architecture supports in-band management of devices over user-defined VRFs.
• Service Traffic Segmentation: Management traffic, such as SNMP and Syslog packets, is segmented across different user-defined VRFs, ensuring separation from other network operations and enhancing security.
• Multi-VRF Support for Protocols: SSH and NETCONF services support connections from multiple VRFs simultaneously, allowing for scalable management across complex networks.
Glossary
The following list provides definitions for key terms or abbreviations and their meanings used throughout this document:
Key Terms/Acronym | Description |
Virtual Routing and Forwarding (VRF) | A technology that allows multiple instances of a routing table to coexist on the same router. Each VRF operates independently, enabling isolated network paths and address spaces within a single physical infrastructure. |
Multiprotocol Label Switching (MPLS) | A method for forwarding packets based on labels rather than network addresses. MPLS is commonly used in conjunction with VRF to route traffic through the network efficiently. |
Label Distribution Protocol (LDP) | A protocol used in MPLS networks to establish label-switched paths (LSPs). LDP is responsible for distributing labels between routers to forward packets in an MPLS environment. |
Open Shortest Path First (OSPF) | A link-state interior gateway protocol (IGP) used to distribute IP routing information within a single autonomous system. It is commonly used in conjunction with VRFs to handle routing within a VRF instance. |
Border Gateway Protocol (BGP) | The protocol used to exchange routing information between different autonomous systems. When combined with VRFs, BGP can handle VPNv4 and VPNv6 routes for isolated routing domains. |
Secure Shell (SSH) | A protocol that provides secure access to network devices and systems. In a VRF configuration, SSH can be enabled per VRF, allowing secure management access to routers on a per-VRF basis. |