NetConf Port Access Control
Overview
NetConf is a software tool that provides a mechanism to configure and manage remote network devices seamlessly. It uses a simple Remote Procedure Call (RPC) mechanism to facilitate communication between a client and a server.
During the OcNOS installation, the NetConf subsystem called “netconf” is installed. It runs on the default access port 830 over SSH and port 6513 over TLS.
Typically, these default access ports are not configurable and controlled. The NetConf port access control feature enhancement ensures that the Netconf-SSH and NetConf-TLS port access can be controlled and configurable through the new CLIs introduced in the 6.4.1 release.
The following are the new CLIs introduced to support the NetConf port access control:
The following existing CLI is updated to support the NetConf port access control
Feature Characteristics
• This feature allows access control capabilities for the NetConf-SSH and NetConf-TLS ports.
• Enabling/disabling the port.
• Changing the default port.
• Accessing and controlling the NetConf services through Inband and Outband.
• Applying ACL rules to the NetConf port to control its access.
Benefits
This feature enables the user to control the NetConf port access and change the default port.
Configuration
To configure either NetConf-SSH port or the NetConf-TLS port, perform the following steps. After completing the steps you will be configured with a port for NetConf.
1. Disable netconf-ssh and netconf-tls feature
2. Configure port for netconf-ssh and netconf-tls
3. Enable netconf-ssh and netconf-tls feature
Topology
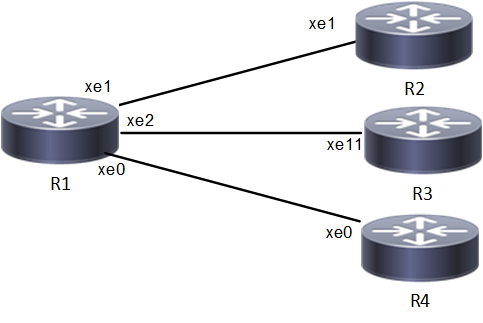
NetConf Accses Port Topology
Enable Netconf-ssh on the default and vrf management port
R1
#configure terminal | Enter Configuration mode. |
R1(config)#feature netconf-ssh | Enable netconf-ssh via default port. |
R1(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port. |
R1(config)#commit | Commit all the transactions. |
Enable Netconf-tls on the default and vrf management port
R1
#configure terminal | Enter Configuration mode |
R1(config)#feature netconf-tls | Enable netconf-tls via default port |
R1(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
Validation
Execute the below commands to verify the NetConf port is enabled on VRF Management.
Following is the output of the NetConf server status and port.
#show netconf server
VRF Management
Netconf SSH Server: Enabled
SSH-Netconf Port : 830
Netconf TLS Server: Enabled
TLS-Netconf Port : 6513
VRF Default
Netconf SSH Server: Enabled
SSH-Netconf Port : 830
Netconf TLS Server: Enabled
TLS-Netconf Port : 6513
Following is the output of NetConf server configurations.
#show running-config netconf-server
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
netconf server ssh-port 2000 vrf management
netconf server tls-port 60000 vrf management
feature netconf-ssh
feature netconf-tls
netconf server ssh-port 1060
netconf server tls-port 5000
!
Following is the output of the NetConf server configuration in XML format.
#show xml running-config
<netconf-server xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-management-serve
r">
<vrfs>
<vrf>
<vrf-name>default</vrf-name>
<config>
<vrf-name>default</vrf-name>
</config>
<netconf-ssh-config>
<config>
<feature-netconf-ssh>true</feature-netconf-ssh>
<ssh-port>1060</ssh-port>
</config>
</netconf-ssh-config>
<netconf-tls-config>
<config>
<feature-netconf-tls>true</feature-netconf-tls>
<tls-port>5000</tls-port>
</config>
</netconf-tls-config>
</vrf>
<vrf>
<vrf-name>management</vrf-name>
<config>
<vrf-name>management</vrf-name>
</config>
<netconf-ssh-config>
<config>
<feature-netconf-ssh>true</feature-netconf-ssh>
<ssh-port>2000</ssh-port>
</config>
</netconf-ssh-config>
<netconf-tls-config>
<config>
<feature-netconf-tls>true</feature-netconf-tls>
<tls-port>60000</tls-port>
</config>
</netconf-tls-config>
</vrf>
</vrfs>
</netconf-server>
<network-instances xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-network-insta
nce">
<network-instance>
<instance-name>default</instance-name>
<instance-type>vrf</instance-type>
<config>
<instance-name>default</instance-name>
<instance-type>vrf</instance-type>
</config>
<vrf xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-vrf">
<config>
<vrf-name>default</vrf-name>
</config>
</vrf>
</network-instance>
<network-instance>
<instance-name>management</instance-name>
<instance-type>vrf</instance-type>
<config>
<instance-name>management</instance-name>
<instance-type>vrf</instance-type>
</config>
<vrf xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-vrf">
<config>
<vrf-name>management</vrf-name>
</config>
</vrf>
</network-instance>
</network-instances>
<interfaces xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-interface">
Following is the output after login to the NetConf interface (YangCLI) on R1 node via the default NetConf port:
root@OcNOS:~# ip netns exec zebosfib0 yangcli --server=127.1 --user=ocnos --password=ocnos
yangcli version 2.5-5
libssh2 version 1.8.0
Copyright (c) 2008-2012, Andy Bierman, All Rights Reserved.
Copyright (c) 2013-2015, Vladimir Vassilev, All Rights Reserved.
Copyright (c) 2012-2016, OpenClovis Inc, All Rights Reserved.
Type 'help' or 'help <command-name>' to get started
Use the <tab> key for command and value completion
Use the <enter> key to accept the default value in brackets
These escape sequences are available when filling parameter values:
? help
?? full help
?s skip current parameter
?c cancel current command
These assignment statements are available when entering commands:
$<varname> = <expr> Local user variable assignment
$$<varname> = <expr> Global user variable assignment
@<filespec> = <expr> File assignment
val->res is NO_ERR.
yangcli: Starting NETCONF session for ocnos on 127.1
NETCONF session established for ocnos on 127.1
…………..
Disable netconf-ssh via default and vrf management port
R1
#configure terminal | Enter Configuration mode |
R1(config)#no feature netconf-ssh | Disable netconf-ssh via default port |
R1(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management |
R1(config)#commit | Commit all the transactions |
Disable netconf-tls via default port and vrf management port
R1
#configure terminal | Enter Configuration mode |
R1(config)#no feature netconf-tls | Disable netconf-tls via default |
R1(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
Validation
Execute the below commands to verify the NetConf port is disabled on VRF Management.
Following is the output of the NetConf server status and port.
#show netconf server
VRF Management
Netconf Server: Disabled
VRF Default
Netconf Server: Disabled
Configuring NetConf Port
R1
#configure terminal | Enter Configuration mode |
R1(config)#no feature netconf-ssh | Disable netconf-ssh via default port |
R1(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management port |
R1(config)#no feature netconf-tls | Disable netconf-tls via default port |
R1(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R1(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R1(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R1(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R1(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R1(config)#feature netconf-tls | Enable netconf-tls via default port |
R1(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
Validation
Following is the output of the NetConf server status and port.
#show netconf server
VRF Management
Netconf SSH Server: Enabled
SSH-Netconf Port : 2000
Netconf TLS Server: Enabled
TLS-Netconf Port : 60000
VRF Default
Netconf SSH Server: Enabled
SSH-Netconf Port : 1060
Netconf TLS Server: Enabled
TLS-Netconf Port : 5000
Following is the output after login to the NetConf interface (YangCLI) on R1 node via the user defined NetConf port:
root@OcNOS:~# ip netns exec zebosfib1 yangcli --server=127.1 --user=ocnos --password=ocnos ncport=2000
Warning: Revision date in the future (2022-08-30), further warnings are suppressed
ietf-netconf-notifications.yang:46.4: warning(421): revision date in the future
yangcli version 2.5-5
libssh2 version 1.8.0
Copyright (c) 2008-2012, Andy Bierman, All Rights Reserved.
Copyright (c) 2013-2015, Vladimir Vassilev, All Rights Reserved.
Copyright (c) 2012-2016, OpenClovis Inc, All Rights Reserved.
Type 'help' or 'help <command-name>' to get started
Use the <tab> key for command and value completion
Use the <enter> key to accept the default value in brackets
These escape sequences are available when filling parameter values:
? help
?? full help
?s skip current parameter
?c cancel current command
These assignment statements are available when entering commands:
$<varname> = <expr> Local user variable assignment
$$<varname> = <expr> Global user variable assignment
@<filespec> = <expr> File assignment
val->res is NO_ERR.
yangcli: Starting NETCONF session for ocnos on 127.1
NETCONF session established for ocnos on 127.1
.........................
Checking Server Modules...
yangcli ocnos@127.1>
Ping between two nodes via Yang CLI
Perform the following configurations to verify the reachability among R1, R2 and R3 routers via NetConf-SSH and NetConf-TLS port.
R1
#configure terminal | Enter Configuration mode |
R1(config)#no feature netconf-ssh | Disable netconf-ssh via default |
R1(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management port |
R1(config)#no feature netconf-tls | Disable netconf-tls via default port |
R1(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R1(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R1(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R1(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R1(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R1(config)#feature netconf-tls | Enable netconf-tls via default port |
R1(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#interface xe1 | Enter interface mode |
R1(config)#ip address 10.10.10.1/24 | Configure ipv4 address on the interface xe1. |
R1(config)#commit | Commit all the transactions |
R2
#configure terminal | Enter Configuration mode |
R2(config)#no feature netconf-ssh | Disable netconf-ssh via default |
R2(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management |
R2(config)#no feature netconf-tls | Disable netconf-tls via default |
R2(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R2(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R2(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R2(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R2(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R2(config)#feature netconf-tls | Enable netconf-tls via default port |
R2(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#interface xe1 | Enter interface mode |
R2(config)#ip address 10.10.10.2/24 | Configure ipv4 address on the interface xe1. |
R2(config)#commit | Commit all the transactions |
Validation
Following is the output of the configured NetConf port.
#show netconf server
VRF Management
Netconf SSH Server: Enabled
SSH-Netconf Port : 2000
Netconf TLS Server: Enabled
TLS-Netconf Port : 60000
VRF Default
Netconf SSH Server: Enabled
SSH-Netconf Port : 1060
Netconf TLS Server: Enabled
TLS-Netconf Port : 5000
OcNOS#show running-config interface xe1
!
interface xe1
ip address 10.10.10.1/24
!
OcNOS#ping 10.10.10.2
Press CTRL+C to exit
PING 10.10.10.2 (10.10.10.2) 56(84) bytes of data.
64 bytes from 10.10.10.2: icmp_seq=1 ttl=64 time=0.567 ms
64 bytes from 10.10.10.2: icmp_seq=2 ttl=64 time=0.258 ms
64 bytes from 10.10.10.2: icmp_seq=3 ttl=64 time=0.241 ms
--- 10.10.10.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 80ms
rtt min/avg/max/mdev = 0.241/0.355/0.567/0.150 ms
Following is the output after login to the NetConf interface (YangCLI) on R2 node through the user defined NetConf port:
root@OcNOS:~# ip netns exec zebosfib0 yangcli --server=10.10.10.2 --user=ocnos --password=ocnos ncport=1060
Warning: Revision date in the future (2022-08-30), further warnings are suppressed
ietf-netconf-notifications.yang:46.4: warning(421): revision date in the future
yangcli version 2.5-5
libssh2 version 1.8.0
Copyright (c) 2008-2012, Andy Bierman, All Rights Reserved.
Copyright (c) 2013-2015, Vladimir Vassilev, All Rights Reserved.
Copyright (c) 2012-2016, OpenClovis Inc, All Rights Reserved.
Type 'help' or 'help <command-name>' to get started
Use the <tab> key for command and value completion
Use the <enter> key to accept the default value in brackets
These escape sequences are available when filling parameter values:
? help
?? full help
?s skip current parameter
?c cancel current command
These assignment statements are available when entering commands:
$<varname> = <expr> Local user variable assignment
$$<varname> = <expr> Global user variable assignment
@<filespec> = <expr> File assignment
val->res is NO_ERR.
yangcli: Starting NETCONF session for ocnos on 10.10.10.2
NETCONF session established for ocnos on 10.10.10.2
..........................
Checking Server Modules...
yangcli ocnos@10.10.10.2>
ACL Rule with IPv4 Configuration
Perform the following configurations to apply an ACL rule to allow or deny traffic from R1 to other nodes via NetConf port.
R1
#configure terminal | Enter Configuration mode |
R1(config)#no feature netconf-ssh | Disable netconf-ssh via default |
R1(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management port |
R1(config)#no feature netconf-tls | Disable netconf-tls via default port |
R1(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R1(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R1(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R1(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R1(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R1(config)#feature netconf-tls | Enable netconf-tls via default port |
R1(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#interface xe1 | Enter interface mode |
R1(config)#ip address 10.10.10.1/24 | Configure ipv4 address on the interface xe1. |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#interface xe2 | Enter interface mode |
R1(config)#ip address 20.20.20.1/24 | Configure ipv4 address on the interface xe2. |
R1(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R1(config)#ip access-list ACL1 | Create ip access list |
R1(config)#permit any host 10.1.1.1 any | Create an acl rule to permit |
R1(config)#deny any host 20.1.1.1 any | Create an acl rule to deny |
R1(config)#commit | Commit all the transactions |
R2
Perform the following configurations to apply an ACL rule to allow or deny traffic from R2 to other nodes via NetConf port
#configure terminal | Enter Configuration mode |
R2(config)#no feature netconf-ssh | Disable netconf-ssh via default |
R2(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management |
R2(config)#no feature netconf-tls | Disable netconf-tls via default |
R2(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R2(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R2(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R2(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R2(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R2(config)#feature netconf-tls | Enable netconf-tls via default port |
R2(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R2(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R2(config)#interface xe1 | Enter interface mode |
R2(config)#ip address 10.10.10.2/24 | Configure ipv4 address on the interface xe1. |
R2(config)#commit | Commit all the transactions |
R3
Perform the following configurations to apply an ACL rule to allow or deny traffic from R3 to other nodes via NetConf port.
#configure terminal | Enter Configuration mode |
R3(config)#no feature netconf-ssh | Disable netconf-ssh via default |
R3(config)#no feature netconf-ssh vrf management | Disable netconf-ssh via vrf management port |
R3(config)#no feature netconf-tls | Disable netconf-tls via default port |
R3(config)#no feature netconf-tls vrf management | Disable netconf-tls via vrf management port |
R3(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R3(config)#netconf server ssh-port 1060 | Configure port for netconf-ssh default |
R3(config)#netconf server ssh-port 2000 vrf management | Configure port for netconf-ssh vrf management |
R3(config)#netconf server tls-port 5000 | Configure port for netconf-tls default |
R3(config)#netconf server tls-port 60000 vrf management | Configure port for netconf-tls vrf management |
R3(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R3(config)#feature netconf-ssh | Enable netconf-ssh via default port |
R3(config)#feature netconf-ssh vrf management | Enable netconf-ssh via vrf management port |
R3(config)#feature netconf-tls | Enable netconf-tls via default port |
R3(config)#feature netconf-tls vrf management | Enable netconf-tls via vrf management port |
R3(config)#commit | Commit all the transactions |
#configure terminal | Enter Configuration mode |
R3(config)#interface xe11 | Enter interface mode |
R3(config)#ip address 20.20.20.2/24 | Configure ipv4 address on the interface xe11. |
R3(config)#commit | Commit all the transactions |
Validation
Following is the output to verify the user defined NetConf port.
R1#show running-config netconf-server
!
feature netconf-ssh vrf management
feature netconf-tls vrf management
netconf server ssh-port 2000 vrf management
netconf server tls-port 60000 vrf management
feature netconf-ssh
feature netconf-tls
netconf server ssh-port 1060
netconf server tls-port 5000
!
R1#show netconf server
VRF Management
Netconf SSH Server: Enabled
SSH-Netconf Port : 2000
Netconf TLS Server: Enabled
TLS-Netconf Port : 60000
VRF Default
Netconf SSH Server: Enabled
SSH-Netconf Port : 1060
Netconf TLS Server: Enabled
TLS-Netconf Port : 5000
Following is the output of the show running-config in XML format.
R1#show xml running-config
<netconf-server xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-management-serve
r">
<vrfs>
<vrf>
<vrf-name>default</vrf-name>
<config>
<vrf-name>default</vrf-name>
</config>
<netconf-ssh-config>
<config>
<feature-netconf-ssh>true</feature-netconf-ssh>
<ssh-port>1060</ssh-port>
</config>
</netconf-ssh-config>
<netconf-tls-config>
<config>
<feature-netconf-tls>true</feature-netconf-tls>
<tls-port>5000</tls-port>
</config>
</netconf-tls-config>
</vrf>
<vrf>
<vrf-name>management</vrf-name>
<config>
<vrf-name>management</vrf-name>
</config>
<netconf-ssh-config>
<config>
<feature-netconf-ssh>true</feature-netconf-ssh>
<ssh-port>2000</ssh-port>
</config>
</netconf-ssh-config>
<netconf-tls-config>
<config>
<feature-netconf-tls>true</feature-netconf-tls>
<tls-port>60000</tls-port>
</config>
</netconf-tls-config>
</vrf>
</vrfs>
</netconf-server>
<network-instances xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-network-insta
nce">
<network-instance>
<instance-name>default</instance-name>
<instance-type>vrf</instance-type>
<config>
<instance-name>default</instance-name>
<instance-type>vrf</instance-type>
</config>
<vrf xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-vrf">
<config>
<vrf-name>default</vrf-name>
</config>
</vrf>
</network-instance>
<network-instance>
<instance-name>management</instance-name>
<instance-type>vrf</instance-type>
<config>
<instance-name>management</instance-name>
<instance-type>vrf</instance-type>
</config>
<vrf xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-vrf">
<config>
<vrf-name>management</vrf-name>
</config>
</vrf>
</network-instance>
</network-instances>
<interfaces xmlns="http://www.ipinfusion.com/yang/ocnos/ipi-interface">
Implementation Examples
The below examples are based on the topology given in Topology section.
Accessing R1 from R2 with default port
Below is an example to access R1 from R2 with default port.
From OcNOS CLI:
feature netconf-ssh
feature netconf-ssh vrf management
feature netconf-tls
feature netconf-tls vrf management
From Yang CLI:
root@OcNOS:~# ip netns exec zebosfib0 yangcli --server=127.1 --user=ocnos --password=ocnos
Accessing R1 from R2 with user defined port
Below is an example to access R1 from R2 via user defined port.
From OcNOS CLI:
netconf server ssh-port 1060
netconf server ssh-port 2000 vrf management
netconf server tls-port 5000
netconf server tls-port 60000 vrf management
From Yang CLI:
root@OcNOS:~#ip netns exec zebosfib1 yangcli --server=10.10.10.1 --user=ocnos --password=ocnos ncport=2000
Applying ACL rule to permit or deny any Node
Below is an example to permit any traffic originating from IP address 10.1.1.1. and deny any traffic originating from 20.1.1.1.
From OcNOS CLI:
ip access-list ACL1
permit any host 10.1.1.1 any
deny any host 20.1.1.1 any
Permitting R2 and denying R3
From Yang CLI:
root@OcNOS:~# ip netns exec zebosfib1 yangcli --server=10.10.10.2 --user=ocnos -- password=ocnos ncport=2000
New CLI Commands
feature netconf-ssh
Use this command to enable or disable the netconf-ssh feature specific to the management VRF. When netconf feature-ssh is enabled, it allows the logins through the default netconf-ssh port or through default ssh port if feature SSH is also enabled.
Command Syntax
feature netconf-ssh (vrf management|)
no feature netconf-ssh (vrf management|)
Parameters
vrf management
Specifies the management Virtual Routing and Forwarding
Default
Disabled by default.
Command Mode
Configure mode
Applicability
This command was introduced in OcNOS version 6.4.1.
Examples
The following example shows you how to enable NetConf SSH on either the VRF management port or the default port. The no parameter disables the same.
(config)#feature netconf-ssh vrf management
(config)#feature netconf-ssh
(config)#no feature netconf-ssh vrf management
(config)#no feature netconf-ssh
#
feature netconf-tls
Use this command to enable or disable the NetConf TLS feature specific to a VRF. When netconf feature-ssh is enabled, it allows the logins through the default netconf-tls port and allows login through a default TLS port when the TLS feature is also enabled.
Command Syntax
feature netconf-tls (vrf management|)
no feature netconf-tls (vrf management|)
Parameters
vrf management
Specifies management Virtual Routing and Forwarding.
Default
Disabled by default.
Command Mode
Configure mode
Applicability
This command was introduced in OcNOS version 6.4.1.
Examples
The following example shows how to execute the CLI:
(config)#feature netconf-tls vrf management
(config)#feature netconf-tls
(config)#no feature netconf-tls vrf management
(config)#no feature netconf-tls
If either NetConf SSH or NetConf TLS are disabled one after the other, the following error message will be displayed, % Disabling this will stop the netconf service that is running in management vrf” as shown below.
Management VRF Configuration
OcNOS#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
(config)#no feature netconf-ssh vrf management
(config)#commit
(config)#no feature netconf-tls vrf management
(config)#commit
% Disabling this will stop the netconf service that is running in management vrf.
Default VRF Configuration
OcNOS#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
(config)#no feature netconf-ssh vrf management
(config)#commit
(config)#no feature netconf-tls vrf management
(config)#commit
% Disabling this will stop the netconf service that is running in defualt vrf.
netconf-ssh port
Use this command to either configure or unconfigure the custom NetConf SSH port.
Command Syntax
netconf-server ssh-port <1024-65535> (vrf management|)
no netconf-server ssh-port (vrf management|)
Parameters
<1024-65535>
Port range values
Default
By default, the netconf-ssh port value is 830.
vrf
Specifies the management Virtual Routing and Forwarding name
Command Mode
Config mode
Applicability
This command was introduced in OcNOS version 6.4.1.
Examples
The following example shows how to execute the CLI:
(config)#netconf server ssh-port ?
<1024-65535> port
(config)#netconf server ssh-port 1024 vrf management
(config)#netconf server ssh-port 2000
(config)#no netconf server ssh-port
(config)#no netconf server ssh-port vrf management
netconf-tls port
Use this command to either configure or unconfigure the indicated NetConf TLS port.
Command Syntax
netconf-server tls-port <1024-65535> (vrf management|)
no netconf-server tls-port (vrf management|)
Parameters
<1024-65535>
Port range values
Default
By default, the netconf-tls port value is 6513.
vrf
Specifies the management Virtual Routing and Forwarding name
Command Mode
Config mode
Applicability
This command was introduced in OcNOS version 6.4.1.
Examples
(config)#netconf server tls-port ?
<1024-65535> port
(config)#netconf server tls-port 5000 vrf management
(config)#netconf server tls-port 3000
(config)#no netconf server tls-port vrf management
(config)#no netconf server tls-port
show netconf server
Use this command to display netconf server status.
Command Syntax
show netconf server
Parameters
None
Command Mode
Exec mode
Applicability
This command was introduced before OcNOS version 6.4.1.
Examples
The following example shows the output of the CLI:
OcNOS#show netconf server
VRF MANAGEMENT
Netconf Server: Enabled
SSH-Netconf Port : 1000
TLS-Netconf Port : 7000
VRF DEFAULT
Netconf Server: Enabled
SSH-Netconf Port : 4500
TLS-Netconf Port : 3000
show running-config netconf server
Use this command to display the NetConf server settings that appear in the running configuration.
Command Syntax
show running-config netconf-server
Parameters
None
Command Mode
Exec mode
Applicability
This command was introduced in OcNOS version 6.4.1.
Examples
The following example shows the output of the CLI:
OcNOS#show running-config netconf-server
feature netconf vrf management
netconf server ssh-port 1000 vrf management
netconf server tls-port 7000 vrf management
feature netconf
netconf server ssh-port 4500
netconf server tls-port 3000
!
Revised CLI Commands
The existing ip access-list tcp|udp CLI is updated with the following two options to support the Access List (ACL) rules on the NetConf port. The ACL defines a set of rules to control network traffic and reduce network attacks.
netconf-ssh
Secure Shell Network Configuration
netconf-tls
Transport Layer Security Network Configuration
ip access-list tcp|udp
Use this command to define a named access control list (ACL) that determines whether to accept or drop an incoming TCP or UDP IP packet based on the specified match criteria. This command filters packets based on source and destination IP address along with the TCP or UDP protocol and port.
Use the no form of this command to remove an ACL specification.
Note: Configuring same filter again with change of sequence number or change of action will result in update of sequence number or filter action.
Note: TCP flags options and range options like neq, gt, lt and range are not supported by hardware in egress direction.
Note: Both Ack and established flag in tcp have same functionality in hardware.
Command Syntax
(<1-268435453>|) (deny|permit) tcp (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any) ((eq|gt|lt|neq) (<0-65535>|bgp|chargen|cmd|daytime|discard|domain|drip|echo |exec|finger|ftp |ftp-data|gopher|hostname|ident|irc|klogin|kshell|login |lpd|nntp|pim-auto- rp|pop2|pop3|smtp|ssh|sunrpc|tacacs|talk|telnet|time| uucp|whois|www)| range <0-65535> <0-65535>|) (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any) ((eq|gt|lt|neq) (<0-65535>|bgp|chargen|cmd|daytime|discard|domain| drip|echo|exec|finger|ftp|ftp-data|gopher|hostname|ident|irc|klogin|kshell|login |lpd|nntp|pim-auto- rp|pop2|pop3|smtp|ssh|sunrpc|tacacs|talk|telnet |time|uucp|whois|www|netconf-ssh|netconf-tls) | range <0-65535> <0-65535>|) ((dscp (<0-63>| af11| af12| af13| af21| af22| af23| af31| af32| af33| af41| af42| af43| cs1| cs2| cs3| cs4| cs5| cs6| cs7| default| ef)) |(precedence (<0-7>| critical| flash | flashoverride| immediate| internet| network| priority| routine)) |) ({ack|established|fin|psh|rst|syn|urg}|) vlan <1-4094>|)(inner-vlan <1-4094>|)
(<1-268435453>|) (deny|permit) udp (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any) ((eq|gt|lt|neq) (<0-65535>|biff|bootpc|bootps|discard|dnsix|domain| echo|isakmp|mobile-ip |nameserver | netbios-dgm | netbios-ns| netbios-ss|non500-isakmp|ntp|pim-auto-rp|rip|snmp|snmptrap|sunrpc|syslog|tacacs|talk|tftp |time|who|xdmcp) | range <0-65535> <0-65535>|) (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any) ((eq|gt |lt|neq)(<0-65535> |biff |bootpc |bootps| discard| dnsix| domain| echo| isakmp|mobile-ip|nameserver|netbios-dgm|netbios-ns|netbios-ss|non500-isakmp |ntp|pim-auto- rp| rip| snmp| snmptrap| sunrpc| syslog| tacacs| talk| tftp| time| who| xdmcp) | range <0-65535> <0-65535>|) ((dscp (<0-63>| af11| af12| af13| af21| af22| af23| af31| af32| af33| af41| af42| af43| cs1| cs2| cs3| cs4| cs5| cs6| cs7| default| ef)) | (precedence (<0-7>| critical| flash | flashoverride| immediate| internet| network| priority| routine))|) (vlan <1-4094>|)(inner-vlan <1-4094>|)
no (<1-268435453>|) (deny|permit) tcp (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any)((eq|gt|lt|neq) (<0-65535>| bgp| chargen| cmd| daytime| discard| domain| drip| echo|exec|finger|ftp |ftp-data |gopher |hostname| ident| irc| klogin| kshell|login|lpd|nntp|pim-auto-rp |pop2 |pop3 |smtp| ssh| sunrpc| tacacs |talk|telnet|time|uucp|whois|www|netconf-ssh|netconf-tls) | range <0-65535> <0-65535>|) (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any)((eq|gt|lt|neq) (<0-65535> |bgp |chargen |cmd |daytime|discard|domain|drip|echo|exec|finger|ftp|ftp-data| gopher| hostname| ident| irc| klogin| kshell| login| lpd| nntp| pim-auto-rp | pop2| pop3| smtp |ssh |sunrpc|tacacs|talk|telnet|time|uucp|whois|www) | range <0-65535> <0-65535>|) ((dscp (<0-63>| af11| af12| af13| af21| af22| af23| af31| af32| af33| af41| af42| af43| cs1| cs2| cs3| cs4| cs5| cs6| cs7| default| ef)) | (precedence (<0-7>| critical| flash | flashoverride| immediate| internet| network| priority| routine)) |) ({ack|established|fin|psh|rst|syn|urg}|)(vlan <1-4094>|)(inner-vlan <1-4094>|)
no (<1-268435453>|)(deny|permit) udp (A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D|any) ((eq|gt|lt|neq) (<0-65535> |biff| bootpc| bootps| discard| dnsix| domain|echo|isakmp|mobile-ip|nameserver|netbios-dgm|netbios-ns|netbios-ss|non500-isakmp|ntp|pim-auto-rp|rip|snmp|snmptrap|sunrpc|syslog|tacacs|talk| tftp|time|who|xdmcp) | range <0-65535> <0-65535>|)(A.B.C.D/M|A.B.C.D A.B.C.D|host A.B.C.D| any) ((eq|gt|lt|neq) (<0-65535> |biff| bootpc| bootps| discard| dnsix| domain|echo| isakmp|mobile- ip|nameserver|netbios-dgm|netbios-ns|netbios-ss|non500-isakmp| ntp|pim-auto-rp|rip|snmp|snmptrap|sunrpc|syslog| tacacs|talk|tftp|time|who|xdmcp) | range <0-65535> <0-65535>|) ((dscp (<0-63>| af11| af12| af13| af21| af22| af23| af31| af32| af33| af41| af42| af43| cs1| cs2| cs3| cs4| cs5| cs6| cs7| default| ef)) | (precedence (<0-7>| critical| flash | flashoverride| immediate| internet| network| priority| routine)) |)(vlan <1-4094>|)(inner-vlan <1-4094>|)
Parameters
<1-268435453>
IPv4 ACL sequence number.
deny
Drop the packet.
permit
Accept the packet.
tcp
Transmission Control Protocol.
udp
User Datagram Protocol.
A.B.C.D/M
Source or destination IP prefix and length.
A.B.C.D A.B.C.D
Source or destination IP address and mask.
host A.B.C.D
Source or destination host IP address.
any
Any source or destination IP address.
eq
Source or destination port equal to.
gt
Source or destination port greater than.
lt
Source or destination port less than.
neq
Source or destination port not equal to.
<0-65535>
Source or destination port number.
range
Range of source or destination port numbers:
<0-65535>
Lowest value in the range.
<0-65535>
Highest value in the range.
bgp
Border Gateway Protocol.
chargen
Character generator.
cmd
Remote commands.
daytime
Daytime.
discard
Discard.
domain
Domain Name Service.
drip
Dynamic Routing Information Protocol.
echo
Echo.
exec
EXEC.
finger
Finger.
ftp
File Transfer Protocol.
ftp-data
FTP data connections.
gopher
Gopher.
hostname
NIC hostname server.
ident
Ident Protocol.
irc
Internet Relay Chat.
klogin
Kerberos login.
kshell
Kerberos shell.
login
Login.
lpd
Printer service.
nntp
Network News Transport Protocol.
pim-auto-rp
PIM Auto-RP.
pop2
Post Office Protocol v2.
pop3
Post Office Protocol v3.
smtp
Simple Mail Transport Protocol.
ssh
Secure Shell.
sunrpc
Sun Remote Procedure Call.
tacacs
TAC Access Control System.
talk
Talk.
telnet
Telnet.
time
Time.
uucp
UNIX-to-UNIX Copy Program.
whois
WHOIS/NICNAME
www
World Wide Web.
netconf-ssh
Secure Shell Network Configuration
netconf-tls
Transport Layer Security Network Configuration
nntp
Range of source or destination port numbers:
dscp
Match packets with given DSCP value.
<0-63>
Enter DSCP value between 0-63.
af11
AF11 DSCP (001010) decimal value 10.
af12
AF12 DSCP (001100) decimal value 12.
af13
AF13 DSCP (001110) decimal value 14.
af21
AF21 DSCP (010010) decimal value 18.
af22
AF22 DSCP (010100) decimal value 20.
af23
AF23 DSCP (010110) decimal value 22.
af31
AF31 DSCP (011010) decimal value 26.
af32
AF32 DSCP (011100) decimal value 28.
af33
AF33 DSCP (011110) decimal value 30.
af41
AF41 DSCP (100010) decimal value 34.
af42
AF42 DSCP (100100) decimal value 36.
af43
AF43 DSCP (100110) decimal value 38.
cs1
CS1 (precedence 1) DSCP (001000) decimal value 8.
cs2
CS2 (precedence 2) DSCP (010000) decimal value 16.
cs3
CS3 (precedence 3) DSCP (011000) decimal value 24.
cs4
CS4 (precedence 4) DSCP (100000) decimal value 32.
cs5
CS5 (precedence 5) DSCP (101000) decimal value 40.
cs6
CS6 (precedence 6) DSCP (110000) decimal value 48.
cs7
CS7 (precedence 7) DSCP (111000) decimal value 56.
default
Default DSCP (000000) decimal value 0.
ef
EF DSCP (101110) decimal value 46.
precedence
Match packets with given precedence value.
<0-7>
Precedence.
critical
Match packets with critical precedence (5).
flash
Match packets with flash precedence (3).
flashoverride
Match packets with flash override precedence (4).
immediate
Match packets with immediate precedence (2).
internet
Match packets with internetwork control precedence (6).
network
Match packets with network control precedence (7).
priority
Match packets with priority precedence (1).
routine
Match packets with routine precedence (0).
ack
Match on the Acknowledgment (ack) bit.
established
Matches only packets that belong to an established TCP connection.
fin
Match on the Finish (fin) bit.
psh
Match on the Push (psh) bit.
rst
Match on the Reset (rst) bit.
syn
Match on the Synchronize (syn) bit.
urg
Match on the Urgent (urg) bit.
biff
Biff.
bootpc
Bootstrap Protocol (BOOTP) client.
bootps
Bootstrap Protocol (BOOTP) server.
discard
Discard.
dnsix
DNSIX security protocol auditing.
domain
Domain Name Service.
echo
Echo.
isakmp
Internet Security Association and Key Management Protocol.
mobile-ip
Mobile IP registration.
nameserver
IEN116 name service.
netbios-dgm
Net BIOS datagram service.
netbios-ns
Net BIOS name service.
netbios-ss
Net BIOS session service.
non500-isakmp
Non500-Internet Security Association and Key Management Protocol.
ntp
Network Time Protocol.
pim-auto-rp
PIM Auto-RP.
rip
Routing Information Protocol.
snmp
Simple Network Management Protocol.
snmptrap
SNMP Traps.
sunrpc
Sun Remote Procedure Call.
syslogS
ystem Logger.
tacacs
TAC Access Control System.
talk
Talk.
tftp
Trivial File Transfer Protocol.
time
Time.
who
Who service.
xdmcp
X Display Manager Control Protocol.
vlan
Match packets with given vlan value.
<1-4094>
VLAN identifier.
inner-vlan
Match packets with given inner vlan value.
<1-4094>
VLAN identifier.
Default
No default value is specified.
Command Mode
IP access-list mode
Applicability
This command was introduced before OcNOS version 1.3.
Examples
The following is an example to execute the CLI:
#configure terminal
(config)#ip access-list ip-acl-02
(config-ip-acl)#deny udp any any eq tftp
(config-ip-acl)#deny tcp any any eq ssh
(config-ip-acl)#end.
Abbreviations
Acronym | Description |
|---|---|
ACL | Access control list |
RPC | Remote Procedure Call |
SSH | Secure Shell |
TLS | Transport Layer Security |