DHCP Snooping
Overview
DHCP snooping is a series of techniques applied to ensure the security of an existing DHCP infrastructure. It is a security feature that acts like a fire wall between untrusted hosts and trusted DHCP servers. It is a layer-2 security technology built into the operating system of a capable network switch that drops DHCP traffic determined to be unacceptable.
The fundamental use case of DHCP snooping is to prevent unauthorized (rogue) DHCP servers offering IP addresses to DHCP clients. Rogue DHCP servers are often used in ‘man-in the middle’ or ‘Denial of Service’ attacks from malicious purpose. Similarly DHCP clients (rogue) can also cause ‘Denial of Service’ attacks by continuously requesting for IP addresses causing address depletion in the DHCP server.
The DHCP snooping feature performs the following activities:
• Validates DHCP messages received from un-trusted sources and filters out invalid messages.
• Rate-limits DHCP traffic from trusted and un-trusted sources.
• Builds and maintains the DHCP snooping binding database, which contains information about un-trusted hosts with leased IP addresses.
• Utilizes the DHCP snooping binding database to validate subsequent requests from un-trusted hosts.
• To retain the DHCP snooping bindings database across reloads, it is stored in a persistent file on switch itself. Upon reload, the switch restores binding database from the persistent file. On NTP sync, the lease time of the binding entries gets re-adjusted based on the timestamp that was written in the persistent file. The switch keeps the file updated by writing to the file periodically (default interval 300 seconds).
Note: To ensure the accuracy of lease time adjustment, NTP should be configured on the snooper.
• When DHCP snooping is used over MLAG, the DHCP snooping binding database syncing will be happening among the peers via IDL.
DHCP snooping with provider bridge is not supported.
DHCP snooping is enabled on a per-VLAN basis. By default, the feature is inactive on all VLANs. You can enable the feature on a single VLAN or a range of VLANs.
Topology
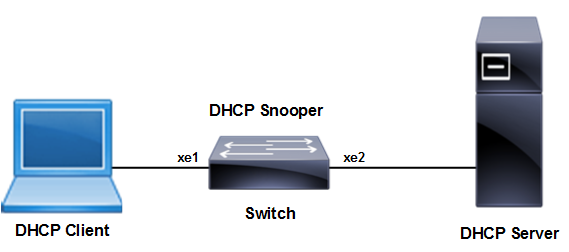
DHCP snooping
Configuration Guidelines
When configuring DHCP snooping, follow these guidelines:
• DHCP snooping is not active until you enable the feature on at least one VLAN, and enable DHCP snooping globally on the switch.
• Before globally enabling DHCP snooping on the switch, make sure that the device acting as the DHCP server is configured and enabled.
• If a Layer 2 LAN port is connected to a DHCP server, configure the port as trusted by entering the ip dhcp snooping trust interface configuration command.
• If a Layer 2 LAN port is connected to a DHCP client, configure the port as un-trusted by entering the no ip dhcp snooping trust interface configuration command.
Procedures
The following subsections provide examples of how to enable and configure DHCP Snooping.
Enable DHCP Snooping Globally
#configure terminal | Enter configure mode. |
(config)#bridge 1 protocol mstp | Create mstp or ieee vlan-bridge. |
(config)#ip dhcp snooping bridge 1 | Enable DHCP Snooping on the bridge |
Enable DHCP Snooping on a VLAN
configure terminal | Enter configure mode. |
(config)#vlan 2 bridge 1 | Configure a vlan for the bridge. |
(config)#ip dhcp snooping vlan 2 bridge 1 | Enable DHCP Snooping on the vlan 2 |
Configure Ports connected to DHCP Sserver and DHCP Client
#configure terminal | Enter the configure mode |
(config)#interface xe1 | Specify the interface xe1 to be configured, and Enter interface mode |
(config-if)#switchport | Configure the interface as a switch port. |
(config-if)#bridge-group 1 | Associate the interface xe1 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port |
(config-if)#switchport access vlan 2 | Bind the interface vlan 2 to the port. |
(config-if)#exit | Exit interface mode. |
(config)#interface xe2 | Specify interface xe2 to be configured connected to server. |
(config-if)#switchport | Configure the interface as a switch port. |
(config-if)#bridge-group 1 | Associate interface xe2 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port. |
(config-if)#switchport access vlan 2 | Bind the interface vlan 2 to the port. |
(config-if)#exit | Exit interface mode. |
(config)#exit | Exit the config mode. |
Configure Trusted and Untrusted Ports
Usually the port connected to server is configured as trusted port and the ports connected to client is configured as untrusted port
In this example, xe1 is connected to the DHCP client and xe2 is connected to the DHCP server.
• Configure xe1 connected to DHCP client as un-trusted port.
• Configure xe2 connected to the DHCP server as trusted port.
#configure terminal | Enter configure mode. |
(config)#interface xe1 | Specify the interface to be configured |
(config-if)#no ip dhcp snooping trust | Disable the port as trusted. |
DHCP Snooping Operation
1. Configure DHCP server that is connected to DHCP Snooper through trusted port.
2. Request an ip address from the DHCP client connected through the un-trusted port.
3. DHCP client broadcast the DHCP DISCOVER message to the switch.
4. DHCP server responds to the DHCP DISCOVER message with DHCP offer message to the client.
5. Once the DHCP OFFER is received by the client, it sends an DHCP REQUEST to the server.
6. DHCP server validates the request from the client and sends DHCP ACK with the offered ip address to the client with the lease time.
7. DHCP Snooper creates an entry for the above operation into the binding table which includes the MAC address of the host, the leased IP address, the lease time, the binding type, and the VLAN number and interface information associated with the host.
8. DHCP Snooper clears the entry in the binding table once the client sends the DHCP RELEASE or lease time is expired.
Note: On snooper once lease time becomes 0 for an entry, it is removed from the bind table within 10 sec.
Validation
The show running-config ip dhcp snooping command displays the DHCP snooping commands configured on the device in question.
#show running-config ip dhcp snooping
!
!
ip dhcp snooping bridge 1
ip dhcp snooping vlan 2 bridge 1
interface xe2
ip dhcp snooping trust
!
The show ip dhcp snooping bridge 1 command displays the configured information about DHCP Snooping.
#show ip dhcp snooping bridge 1
Bridge Group : 1
DHCP snooping is : Enabled
DHCP snooping option82 is : Disabled
Verification of hwaddr field is : Disabled
Strict validation of DHCP packet is : Disabled
Rate limit(pps) : 200
DB Write Interval(secs) : 300
DHCP snooping is configured on following VLANs : 2
DHCP snooping is operational on following VLANs : 2
DHCP snooping IP Source Guard is configured on the following Interface
Interface Trusted
--------------- -------
xe2 Yes
The show ip dhcp snooping binding bridge 1 command displays the binding table entries associated with un-trusted interfaces.
#show ip dhcp snooping bridge 1
Bridge Group : 1
DHCP snooping is : Enabled
DHCP snooping option82 is : Disabled
Verification of hwaddr field is : Disabled
Strict validation of DHCP packet is : Disabled
Rate limit(pps) : 200
DB Write Interval(secs) : 300
DHCP snooping is configured on following VLANs : 2
DHCP snooping is operational on following VLANs : 2
DHCP snooping trust is configured on the following Interfaces
Interface Trusted
-------- -------
xe2 Yes
DHCP snooping IP Source Guard is configured on the following Interfaces
Interface Source Guard
--------------- ------------
DHCP Snooping with Option-82
When DHCP snooping with Option-82 is enabled on the switch, following behavior is expected:
1. The host generates a DHCP request and broadcasts it on the network.
2. When the switch receives DHCP request, it adds option-82 information in the packet.
3. If the IP address of the relay agent is configured, the switch adds the IP address in the DHCP packet.
4. The switch forwards the DHCP request that includes the option-82 field to the DHCP server.
5. The DHCP server receives the packet. If the server is option-82 capable, it can use the information in the option-82 fields to assign IP addresses and implement policies, such as restricting the number of IP addresses that can be assigned to a single remote ID or circuit ID. The DHCP server then echoes the option-82 field in the DHCP reply.
6. The DHCP server unicasts the reply to the switch if the request was relayed to the server by the switch. When the client and server are on the same subnet, the server broadcasts the reply. The switch verifies that it originally inserted the option-82 data by inspecting the remote id and circuit id fields. The switch removes the option-82 field and forwards the packet to the switch port that connects to DHCP client that sent the DHCP request.
Procedures
The following subsections provide examples of how to configure DHCP snooping with option-82.
The topology is the same as Figure 4-19.
Enable DHCP Snooping Globally
#configure terminal | Enter configure mode. |
(config)#bridge 1 protocol mstp | Create mstp or ieee vlan-bridge. |
(config)#ip dhcp snooping bridge 1 | Enable DHCP Snooping on the bridge |
Enable DHCP Snooping on a VLAN
configure terminal | Enter configure mode. |
(config)#vlan 2 bridge 1 | Configure a vlan for the bridge. |
(config)#ip dhcp snooping vlan 2 bridge 1 | Enable DHCP Snooping on the vlan 2 |
Configure Ports connected to DHCP Server and DHCP Client
#configure terminal | Enter the configure mode |
(config)#interface xe1 | Specify the interface xe1 to be configured, connected to client and Enter interface mode |
(config-if)#switchport | Configure the interface as a switch port. |
(config-if)#bridge-group 1 | Associate the interface xe1 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port |
(config-if)#switchport access vlan 2 | Bind the interface vlan 2 to the port. |
(config-if)#exit | Exit interface mode. |
(config)#interface xe2 | Specify interface xe2 to be configured connected to server. |
(config-if)#switchport | Configure the interface as a switch port. |
(config-if)#bridge-group 1 | Associate interface xe2 with bridge-group 1. |
(config-if)#switchport mode access | Configure the port as an access port. |
(config-if)#switchport access vlan 2 | Bind the interface vlan 2 to the port. |
(config-if)#exit | Exit interface mode. |
(config)#exit | Exit the config mode. |
Configure Trusted and Untrusted Ports
Usually the port connected to server is configured as trusted port and the ports connected to client is configured as untrusted port
In this example, xe1 is connected to the DHCP client and xe2 is connected to the DHCP server.
• Configure xe1 connected to DHCP client as un-trusted port.
• Configure xe2 connected to the DHCP server as trusted port.
#configure terminal | Enter configure mode. |
(config)#interface xe1 | Specify the interface to be configured |
(config-if)#no ip dhcp snooping trust | Disable the port as trusted. |
#configure terminal | Enter configure mode. |
(config)#interface xe2 | Specify the interface to be configured |
(config-if)#ip dhcp snooping trust | Enable the port as trusted. |
Enable option-82
#configure terminal | Enter configure mode. |
(config)# ip dhcp snooping information option bridge 1 | Configure DHCP snooping information option-82 |
Validation
The show running-config ip dhcp snooping command displays the DHCP snooping commands configured on the device.
#show running-config ip dhcp snooping
!
!
ip dhcp snooping bridge 1
ip dhcp snooping information option bridge 1
ip dhcp snooping vlan 2 bridge 1
interface xe2
ip dhcp snooping trust
!
#show ip dhcp snooping bridge 1
Bridge Group : 1
DHCP snooping is : Enabled
DHCP snooping option82 is : Enabled
Verification of hwaddr field is : Disabled
Strict validation of DHCP packet is : Disabled
Rate limit(pps) : 200
DB Write Interval(secs) : 300
DHCP snooping is configured on following VLANs : 2
DHCP snooping is operational on following VLANs : 2
DHCP snooping trust is configured on the following Interfaces
Interface Trusted
--------------- -------
xe2 Yes
DHCP snooping IP Source Guard is configured on the following Interfaces
Interface Source Guard
--------------- ------------
#show ip dhcp snooping binding bridge 1
Total number of static IPV4 entries : 0
Total number of dynamic IPV4 entries : 1
Total number of static IPV6 entries : 0
Total number of dynamic IPV6 entries : 0
MacAddress IpAddress Lease (sec) Type VLAN Interface
------------------ --------------- ---------- ----------------- ------- -----------
6400.6afc.3ba1 192.168.1.2 600 dhcp-snooping 2 xe1
Sample server dhcpd.conf for option-82
This example shows a server dhcpd.conf file for option-82 with remote-id and circuit-id suboptions.
Remote-id :
class "remote-id" {
match if option agent.remote-id = cc:37:ab:56:6d:80;--->Points to Snooping switch eth0 Mac address.
} # remote-id
subnet 192.168.1.0 netmask 255.255.255.0 {
pool {
option subnet-mask 255.255.255.0;
allow members of "remote-id";
range 192.168.1.2 192.168.1.100;
default-lease-time 600;
max-lease-time 600;
option subnet-mask 255.255.255.0;
option domain-name "Domain1.com";
option domain-name-servers 23.32.23.32,4.4.4.2;
option ntp-servers 19.91.19.91,45.54.45.54,localhost1,19.91.19.91;
option log-servers 10.12.16.17,10.12.16.16;
option bootfile-name "Bootfile1";
option tftp-server-name "Tftpserver1";
option host-name "Omega";
}
}
Circuit-id:
class "circuit-id" {
match if option agent.circuit-id = 00:00:13:b6:00:02;---->Points to vlan and interface index value.
} # circuit-id
subnet 192.168.1.0 netmask 255.255.255.0 {
pool {
option subnet-mask 255.255.255.0;
allow members of "circuit-id";
range 192.168.1.2 192.168.1.100;
default-lease-time 600;
max-lease-time 600;
option subnet-mask 255.255.255.0;
option domain-name "Domain1.com";
option domain-name-servers 23.32.23.32,4.4.4.2;
option ntp-servers 19.91.19.91,45.54.45.54,localhost1,19.91.19.91;
option log-servers 10.12.16.17,10.12.16.16;
option bootfile-name "Bootfile1";
option tftp-server-name "Tftpserver1";
option host-name "Omega";
}
}